OSINT Tools Comparison
An in-depth analysis of the current state of the OSINT tools market, highlighting the importance of Open Source Intelligence (OSINT) in modern security intelligence. It outlines the key components of an effective OSINT solution, including data collection, analysis, visualization, real-time monitoring, and integration capabilities.
Open Source Intelligence (OSINT) refers to the process of collecting, analyzing, and utilizing publicly available information to produce actionable intelligence. This information can come from a variety of sources, including social media, news articles, blogs, forums, and other online platforms. OSINT is a crucial component of modern security intelligence, as it helps organizations identify potential threats, monitor emerging risks, and make informed decisions.
The market for Open Source Intelligence (OSINT) tools is rapidly evolving, driven by the increasing need for comprehensive and actionable intelligence to protect employees and business operations.
Buyers in the market for robust OSINT solutions should be looking for several key features to ensure they are investing in the most effective tools, including:
Competitive pricing
Scalability
Comprehensive suite of tools
Transparency
Integration capabilities
A client-centric approach
Key Components of an OSINT Solution
Data Collection
The first step in an OSINT solution is gathering data from various open sources. This includes scraping websites, monitoring social media platforms, and collecting information from public databases. Best-in-breed OSINT tools allow users to configure the searches themselves without needing to reach out to customer support. The goal is to compile a comprehensive dataset that can be analyzed for relevant insights.
Data Analysis
Once the data is collected, it needs to be analyzed to extract meaningful information. This involves using advanced algorithms and machine learning techniques to identify patterns, trends, and anomalies. The analysis process helps in transforming raw data into actionable intelligence and assess content of concern.
Data Visualization
To make the intelligence easily understandable, OSINT solutions often include data visualization tools. These tools create visual representations of the data, such as graphs, charts, and maps, which help in identifying key insights at a glance. The best tools also include the ability to effectively filter data to identify just the content of interest.
Real-Time Monitoring
Effective OSINT solutions provide real-time monitoring capabilities. This means continuously scanning open sources for new information and updating the intelligence in real-time. Real-time monitoring is essential for staying ahead of emerging threats and responding quickly to critical events.
Integration Capabilities
OSINT solutions should be able to integrate with other security systems and tools. This ensures that the intelligence can be seamlessly incorporated into the organization’s existing security infrastructure, enhancing overall effectiveness.
Dissemination and Reporting
OSINT solutions should offer tools to assist analysts in drafting their reports. Generative AI can help quickly distil large amounts of raw data so analysts can complete and distribute reports quickly.
Investigations
OSINT tools shouldn't just detect threats: they should also provide a toolkit to help analysts investigate further to better support robust behavioural threat assessments. Comprehensive OSINT solutions can help identify anonymous threat actors and manage persons of interest.
OSINT Solution Providers available today
Signal from Signal Corporation
Dataminr
Liferaft (Navigator)
Samdesk
Flashpoint (Echosec)
Babel Street
Penlink (Cobwebs)
Ontic
Fivecast
Seerist
OSINTCombine (NEXUSXplore)
Signal Corp.
Signal Corp’s OSINT platform stands out in the crowded market with its exceptional blend of affordability, scalability, and comprehensive functionality. Unlike many competitors that charge high fees, Signal offers a cost-effective solution without compromising on features. With prices ranging from $35-60K, Signal provides a competitive alternative to platforms that cost over $100K.
One of the key strengths of Signal cited by its customers is the breadth of sources it can monitor. On the scalability side, while many OSINT platforms charge per user license, Signal grants access to the entire organization, making it an ideal choice for large organizations looking for an affordable yet scalable solution. This approach ensures that protective security becomes a team effort, enhancing overall effectiveness.
Signal’s platform is a true multi-tool, offering a wide range of features that cater to various intelligence needs. From comprehensive data collection and report generation to data visualizations, POI investigations, AI incident detection, and asset alerting, Signal offers a complete solution. This eliminates the need for multiple fragmented tools, saving organizations both time and money.
Transparency is another hallmark of Signal’s offering. In an era where many OSINT solutions operate as black boxes, Signal is transparent about how its platform works and leverages artificial intelligence. This transparency ensures that analysts are well-informed and effective in their roles.
Integration capabilities are also a strong suit for Signal. The platform is designed to plug and play with existing solutions, consolidating data where it’s needed. This can include seamless integration with systems like Everbridge 360, Noggin, Restrata’s resilienceOS, ARCGis/Esri, XMatters, and more.
Signal’s client-centric approach sets it apart from the competition. The company is highly responsive to support requests and is willing to design meaningful features based on client feedback. This commitment to client satisfaction ensures that Signal’s platform continually evolves to meet the operational requirements of its users.
Signal Corp’s OSINT platform offers a compelling combination of competitive pricing, scalability, comprehensive functionality, transparency, integration capabilities, and a client-centric approach. These features make it a standout choice for organizations seeking a robust and reliable OSINT solution.
Signal routinely receives outstanding feedback about its customer service and the operational support/advice its specialists provide.
Dataminr
Dataminr is a real-time information discovery platform that uses AI to analyze public data sources and provide actionable alerts. It is known for its ability to detect breaking news and emerging risks, making it a valuable tool for crisis management and situational awareness.
Liferaft (Navigator)
Liferaft’s Navigator is an OSINT platform designed to help organizations identify and mitigate threats from social media and other online sources. It offers features such as real-time monitoring, geospatial analysis, and search capabilities, making it a comprehensive solution for threat intelligence.
Samdesk
Samdesk is an AI-powered crisis detection platform that provides real-time alerts on critical events worldwide. It leverages social media and other data sources to deliver timely and relevant information, helping organizations respond to emerging threats.
Flashpoint (Echosec)
Flashpoint’s Echosec is an OSINT platform that specializes in deep and dark web monitoring. It provides insights into threat actors and their activities, offering features such as keyword monitoring, geospatial analysis, and data visualization to enhance threat intelligence efforts.
Babel Street
Babel Street is an OSINT platform that offers multilingual text analytics and geospatial analysis. It enables organizations to collect, analyze, and visualize data from various sources, providing insights for threat intelligence and risk management.
Penlink (Cobwebs)
Penlink’s Cobwebs is an OSINT platform that focuses on web intelligence and data extraction. It offers features such as automated data collection, entity extraction, and link analysis, making it a useful tool for investigations and intelligence gathering.
Ontic
Ontic is a protective intelligence platform that integrates data from various sources to provide a comprehensive view of potential threats. It offers features such as real-time alerts, risk assessments, and incident management, helping organizations proactively address security risks.
Fivecast
Fivecast is an OSINT platform that uses AI and machine learning to analyze large volumes of data from open sources. It provides insights into emerging threats, trends, and patterns, offering features such as automated data collection, sentiment analysis, and geospatial visualization.
Seerist
Seerist is an OSINT platform that combines AI and human expertise to deliver real-time threat intelligence. It offers features such as predictive analytics, risk assessments, and incident monitoring, helping organizations stay ahead of potential threats.
OSINTCombine (NEXUSXplore)
OSINTCombine’s NEXUSXplore is an OSINT platform that focuses on data aggregation and analysis. It offers features such as automated data collection, entity extraction, and link analysis, providing valuable insights for investigations and intelligence gathering.
Factal
Factal is a real-time risk intelligence platform that uses AI to monitor global events and provide actionable alerts. It offers features such as real-time monitoring, geospatial analysis, and data visualization, helping organizations respond quickly to emerging threats.
Summary
This comparison provides an in-depth analysis of the current state of the OSINT tools market, highlighting the importance of Open Source Intelligence (OSINT) in modern security intelligence. It outlines the key components of an effective OSINT solution, including data collection, analysis, visualization, real-time monitoring, and integration capabilities.
For further information, contact Signal for a free consultation on your OSINT solution needs, or book a free demo.
The Missing Link in Threat Detection: From Identification to Action
Security intelligence professionals are confronted daily with concerning material: threats, hostile rhetoric, violent ideation. These signals emerge from numerous sources, across a wide variety of platforms including social media, forums, messaging apps, obscure websites.
An OSINT platform is indispensable for detecting threats and identifying persons of interest. But once a threat is identified, does your team know what to do next?
Behavioral Threat Assessment
Security intelligence professionals are confronted daily with concerning material: threats, hostile rhetoric, violent ideation. These signals emerge from numerous sources, across a wide variety of platforms including social media, forums, messaging apps, obscure websites.
An OSINT platform is indispensable for detecting threats and identifying persons of interest. It gathers digital breadcrumbs, indicators of violent intent, and reveals patterns that might otherwise remain hidden. But the crucial question remains: once a threat is identified, does your team know what to do next?
The Complexity of Modern Threat Analysis
Security teams must triage a range of potential threats. In this environment, a critical skill is differentiating between noise and genuine risk. A person ranting online about government corruption might be venting frustration. Another individual, using eerily specific language about a planned act of violence, could pose a real danger. The distinction between the two is subtle but vital.
A well-crafted behavioral threat assessment methodology helps analysts make this distinction with confidence. It provides a structured approach to evaluating risk, identifying warning behaviors, and recognizing escalating patterns that indicate a subject may escalate from rhetoric to violent action.
Threat vs. Pose: A Crucial Distinction
One of the most common mistakes in security assessments is focusing too much on whether someone has made a threat, rather than whether they pose a threat. Decades of research show that many attackers do not explicitly announce their intentions before they act. Instead, they exhibit behaviors - subtle but identifiable markers - that indicate a growing risk of violence.
A behavioral threat assessment isn’t about waiting for an individual to cross a red line. It’s about recognizing the patterns leading up to that moment.
Concerning behaviors might include fixation on a particular individual or organization, obsessive grievances, increasingly aggressive rhetoric, or even logistical steps toward an attack, such as acquiring weapons or conducting surveillance on a target.
The Critical Importance of OSINT
Open-source intelligence is an essential component of modern security operations, but it is not a standalone solution. Identifying a concerning online presence is only the beginning. Effective risk mitigation requires a structured evaluation process that considers multiple dimensions:
Intent: Is the individual merely expressing frustration, or do they exhibit signs of genuine commitment to violence?
Capability: Does the person have access to weapons, training, or the logistical means to follow through?
Opportunity: How close is the subject to their potential target, both physically and logistically?
Behavioral Trajectory: Are they demonstrating escalating patterns of hostility, planning, or preparation?
A sophisticated threat assessment process combines OSINT findings with behavioral analysis to create a comprehensive risk profile.
Recognizing the Warning Behaviors
Certain behaviors serve as indicators that an individual may be escalating toward violence. These warning signs don’t operate in isolation, but collectively contribute to an overall threat profile. Some of the most significant include:
Pathway behavior: Steps toward violence, such as researching past attacks, acquiring weapons, or making logistical preparations.
Fixation: An obsessive preoccupation with a person, ideology, or grievance, especially when it leads to an increasingly hostile tone.
Last-resort language: Statements indicating urgency or a belief that violence is the only remaining option.
Identity and justification: Viewing oneself as a warrior for a cause, adopting an ‘us vs. them’ mentality, or attempting to rationalize violence as necessary or righteous.
From Identification to Intervention
Recognizing these behaviors is just the first step. The real challenge is deciding what comes next. Does the subject require persistent monitoring? Should law enforcement be alerted? Is immediate intervention necessary?
Signal’s Behavioral Threat Assessment Guide provides a structured methodology to navigate these decisions. Drawing from both operational experience and academic research, the guide presents a framework for assessing threats and determining appropriate responses.
Instead of reacting impulsively to every inflammatory statement online, security teams can apply a methodical approach to distinguish between bluster and bona fide threats. This is the missing piece in many security strategies—the bridge between detection and decisive action.
Elevating Security Intelligence
The landscape of threat analysis is evolving. As the volume and complexity of digital threats increase, so must the methodologies used to assess and respond to them. OSINT platforms like Signal provide the necessary tools to surface threats, but structured behavioral assessments are what turn information into actionable intelligence.
Does your team have the expertise to make the right call? Can they confidently distinguish between a hostile but harmless individual and someone with the intent and capability to act? If not, they risk either overreacting to low-level threats or, more dangerously, overlooking real risks until it’s too late.
With the right methodology, security professionals can move beyond mere detection. They can anticipate, assess, and intervene—turning intelligence into prevention.
Want to learn more? Check out our Signal Behavioral Threat Assessment Guide.
The Growing Threat of the Deep and Dark Web
The deep and dark web continue to evolve and fuel a vast range of cybercrime and malicious activity. For businesses, this reality requires a shift in how threats are monitored. Relying on traditional methods to keep track of digital dangers is no longer sufficient. The need for comprehensive, proactive OSINT collection solutions is clear.
The deep and dark web continues to provide a breeding ground for illicit activity. As cybercriminals, extremists, and data thieves become more sophisticated, these online underworlds have evolved into major hubs for bad actors and nefarious online behavior.
The dark web has grown to serve as a breeding ground for ransomware attacks, data breaches, and a variety of other malicious activities that can strike at the heart of any organization.
In August 2024, a cybercriminal group known as USDoD leaked a database on the dark web, offering it for sale at $3.5 million. The compromised data, originally gathered by National Public Data, includes sensitive details like names, addresses, Social Security Numbers, and information about siblings. A class-action lawsuit was filed against National Public Data in Florida, accusing them of failing to adequately protect the data and collecting information from non-public sources without consent.
This is just one of the many recent security incidents tied to activity on the dark web. The issue is no longer whether threats are lurking in these spaces, but rather how businesses can keep an eye on them in an ever-evolving landscape.
What Is the Dark Web?
Many people mistakenly believe that the dark web is a single, cohesive network, but this is inaccurate. It is a sprawling collection of decentralized platforms, each built with the intention of preserving anonymity and secrecy. These platforms are essential to understand if companies are to effectively monitor and mitigate potential threats.
Tor (The Onion Router): The most widely recognized of dark web networks, Tor provides users with layers of encryption designed to conceal their online activity. This network serves as a key venue for cybercriminals to operate undetected.
I2P (Invisible Internet Project): Though less well-known, I2P offers a similarly anonymous environment that’s often used for secure communication, particularly in covert operations or illicit dealings.
ZeroNet: An alternative to traditional web hosting, ZeroNet uses peer-to-peer hosting technology, which further complicates monitoring efforts due to its decentralized nature.
What Is the Deep Web?
While the dark web tends to grab the headlines, the deep web encompasses a much broader and more general collection of online content that is not indexed by search engines. This content is not inherently dangerous, but it often includes areas where illicit activities take place.
Paste sites like Pastebin or Ghostbin are often used to dump and share large datasets, including sensitive or stolen information.
Encrypted messaging apps, including platforms like Telegram and Discord, have become favorites among criminals for their ability to facilitate communication in relative secrecy.
Alternative social media platforms, such as Gab or BitChute, have carved out spaces for extremist groups and the spread of misinformation, far removed from the moderation standards of more mainstream platforms.
Breach forums like Cracked and Nulled have emerged as key marketplaces for stolen credentials, malware, and hacking tools, further fueling the dark web ecosystem.
The Challenge of Accessing and Monitoring the Dark Web
For most businesses, monitoring the deep and dark web is a daunting task. First, internal network policies often block direct access to these areas, leaving security teams with limited insight into potential threats.
Even when access is available, security professionals may lack the specialized tools or expertise necessary to navigate these murky waters.
The sheer volume and unstructured nature of data on these platforms add another layer of complexity. Without the proper resources, businesses can easily miss critical indicators of a cyberattack, a data leak, or a vendor compromise.
Why an Enterprise OSINT Platform Is Essential
This is where an enterprise-level OSINT (Open-Source Intelligence) collection platform like Signal becomes an indispensable asset. A robust OSINT solution gives security teams the ability to proactively monitor threats across the deep and dark web without exposing themselves to unnecessary risks. Here's how a comprehensive platform can support your organization:
Secure, Compliant Access: OSINT platforms like Signal offer compliant, secure access to restricted content. This ensures that security teams can gather intelligence on potential threats without violating company policies or compromising internal network security. They can analyze dark web content without needing to actually access the dark web.
Automated Data Collection: Instead of relying on manual searches and outdated methods, OSINT solutions automate the process of tracking emerging threats. This includes everything from detecting stolen credentials and tracking extremist threats, to identifying ransomware incidents in real time.
Advanced Search and Filtering: With advanced tools for parsing and analyzing vast amounts of unstructured data, an OSINT platform enables analysts to cut through the noise. They can extract relevant intelligence with precision, helping them focus on the most immediate threats.
The Rising Importance of Dark Web Monitoring
As cyber threats become increasingly sophisticated and frequent, simply relying on internal cybersecurity measures is no longer enough. Threat actors can infiltrate via third-party vendors, supply chains, or business partners. A breach in a vendor's system and subsequent dump on the Dark Web, for example, could put your organization at risk, but you might not even know until it’s too late.
Organizations can no longer afford to wait until after the fact to find out if their partners or suppliers have been compromised. As the business landscape becomes more interconnected, proactive intelligence is essential to understand where the vulnerabilities are—and whether your organization is at risk.
Conclusion
The deep and dark web continue to evolve and fuel a vast range of cybercrime and malicious activity. For businesses, this reality requires a shift in how threats are monitored. Relying on traditional methods to keep track of digital dangers is no longer sufficient. The need for comprehensive, proactive OSINT collection solutions is clear.
By incorporating tools like Signal into your security strategy, you gain the ability to navigate the shadows of the internet. It’s a necessity for any organization committed to staying one step ahead of emerging risks.
At Signal, we empower organizations to take control of their cyber defenses with OSINT solutions, enabling you to monitor and respond to dark web threats with speed, accuracy, and confidence.
Enhancing Human Decisions with AI-Powered Insights
Artificial intelligence has enabled us to process and interpret vast amounts of online content more efficiently than ever before in order to make critical decisions based on accurate analysis. By integrating advanced capabilities like generative AI, post categorization, and Named Entity Recognition (NER), Signal’s tools are designed to amplify human expertise, not replace it.
Streamlining Content Categorization
The sheer volume of digital content produced every second makes it increasingly difficult for analysts to identify actionable information. AI can help bridge this gap by recognizing threats of violence, hate speech, and a myriad of other areas of concern and then tagging it for a human analyst’s attention.
Instead of manually sorting through thousands of posts, analysts can rely on these systems to surface what matters most, cutting down noise and focusing their efforts where it’s needed. This level of automation ensures no critical detail slips through the cracks, even during high-pressure scenarios.
At Signal, categorization doesn’t stop at basic filtering. Our technology is designed with analysts' needs in mind, using machine learning models trained on real-world data. These models adapt to recognize the nuances of language and context, whether it’s a vague online threat or coded messages from a particular online community.
By grouping relevant posts together under tailored categories, we help analysts build a comprehensive understanding of any situation in a fraction of the time.
Connecting the Dots with Named Entity Recognition (NER)
Manually identifying key details like names, locations, and organizations across a sea of information is both time-consuming and error-prone. With NER, AI can instantly extract these critical elements from posts, offering a structured overview of the key players and locations involved. This feature enables analysts to see connections and patterns that might otherwise go unnoticed, giving them a head start on piecing together a full narrative.
NER is especially valuable in chaotic situations where details are emerging rapidly. For example, during a breaking news event, analysts can use this capability to identify recurring names or places being mentioned online.
This doesn’t just save time: it creates a foundation for deeper investigations, helping analysts connect information across platforms, conversations, or even geographical areas.
Empowering Analysts with Generative AI
Report writing is a core part of an analyst’s job, but it’s also one of the most time-intensive tasks. Generative AI transforms this process by helping draft initial reports in a polished, professional style. Analysts can input key details and receive a draft that’s ready for refinement, significantly reducing the time between gathering insights and delivering findings to decision-makers.
This capability doesn’t just streamline operations—it improves the quality of reports, too. By automating the more routine aspects of writing, analysts can focus on crafting more thoughtful conclusions or verifying critical details. Whether it’s summarizing complex datasets or generating readable summaries of dense information, generative AI ensures analysts spend their time where it counts: interpreting data and making assessments.
Uniting Fragmented Information
When incidents unfold online, they’re rarely confined to a single post or source. Discussions emerge across platforms, each contributing a piece of the puzzle. Signal’s AI clusters related posts to give analysts a complete, unified view of any event. This capability is particularly important for understanding fast-evolving situations, where isolated snippets of information need to be pieced together into a coherent narrative.
The Global Feed feature - providing next-generation open-source intelligence - takes this even further by providing access to a broad range of publicly available data in real time. By clustering posts and analyzing them collectively, analysts can uncover trends, track the spread of misinformation, or identify emerging threats. These insights are critical for producing reports that don’t just summarize events but also offer context and actionable recommendations.
Actionable Workflows, Timely Outputs
In time-sensitive situations, delays are catastrophic. Signal’s AI tools are built to prioritize speed and accuracy, automating repetitive tasks like post collection, categorization, and clustering. This ensures that workflows remain streamlined and decision-makers receive timely insights to guide their actions.
The impact of timely outputs extends beyond efficiency; it directly influences how decisions are made. Whether it’s responding to a security threat or planning a public relations strategy, actionable intelligence delivered in real time allows teams to act with confidence. Signal’s technology ensures that analysts can keep pace with the speed of the internet, empowering them to deliver insights that matter when they matter most.
AI as an Enabler, Never a Replacer
AI’s potential is transformative, but it’s no substitute for the critical thinking, intuition, and experience that human analysts bring to the table. Tools like Signal are designed to complement—not compete with—human expertise. By automating the most time-intensive tasks, AI enables analysts to focus on higher-value activities, such as interpreting ambiguous data or assessing the nuance of a potential threat.
The human-in-the-loop approach is particularly vital in complex cases, such as assessing threats or identifying patterns that require deeper contextual understanding. While AI provides the tools to speed up workflows and surface critical insights, it’s the analyst’s role to ensure that these insights translate into meaningful actions. At Signal, we believe the best results come from the perfect balance of technology and human expertise.
Try Signal
Want to see these capabilities in action? Request a demo today and discover how Signal’s Global Feed and AI-driven tools can transform your workflow.
Why Transparency is Critical in the Era of 'Black Box' OSINT Solutions
The allure of “one-click magic” solutions is undeniable. A tool that promises comprehensive results at the press of a button? Great. No digging, no deliberating, just answers. It sounds like a dream, doesn’t it? But dreams can quickly turn into nightmares when the methods behind those answers are shrouded in mystery.
As the old saying goes: if it sounds too good to be true, it probably is.
As we move further into an era dominated by artificial intelligence, it is imperative for analysts to demand transparency from “black box” OSINT solutions.
The Hidden Risks of Black Box OSINT
Without a clear understanding of how intelligence results are derived, users are left with little more than blind faith. Consider the consequences in high-stakes industries like journalism, law enforcement, or national security, where a single unverified piece of information could lead to reputational damage, operational failures, and even endanger lives.
Moreover, the very nature of these tools reduces trust in AI-driven solutions. When users are unable to see how conclusions are reached, skepticism grows. This lack of confidence undermines the potential of artificial intelligence to assist in critical decision-making, turning what should be a powerful ally into a questionable crutch.
Users should never be in the dark about the mechanics of their tools. A lack of transparency not only risks operational credibility but also perpetuates the idea that OSINT solutions are “magic” rather than reliable, verifiable systems.
A Beacon of Transparency: the Power of Clear Sourcing
Rather than hiding behind proprietary algorithms and secretive processes, Signal’s Global Feed platform provides users with interactive dashboards and traceable data points, making it easier to cross-verify intelligence. This proactive transparency is a game changer in an industry plagued by ambiguity.
Transparency begins with an honest discussion of AI’s capabilities and limitations. Global Feed doesn’t sell illusions. Instead, it equips users with a clear picture of what AI can achieve, alongside its potential pitfalls. This openness allows users to navigate the complexities of OSINT with confidence, rather than uncertainty.
Global Feed also incorporates the Admiralty Scale, a trusted method from the intelligence community, to evaluate the confidence and credibility of its sources. This approach not only ensures accuracy but also fosters a deeper understanding of the data’s nuances.
Why Transparency Fosters Trust
Trust is the currency of effective intelligence, and transparency is its foundation. But trust doesn’t come from blind faith; it’s earned through understanding. Global Feed recognizes this and prioritizes user awareness at every step.
By providing clarity and openness on its methodologies, Global Feed demystifies the process of AI-driven intelligence. Users don’t need to be experts in machine learning to grasp the basics of how the platform works. This accessibility empowers users to make informed decisions, rather than relying on the supposed infallibility of a machine.
This transparency creates an environment where users can not only trust their tools but also feel empowered to justify their decisions to stakeholders. The combination of clear sourcing, intuitive tools, and ethical AI use sets a new standard for OSINT platforms.
The Future of OSINT Lies in the Open
The world of OSINT is at a crossroads. On one side, we have black-box solutions that promise simplicity but deliver opacity. On the other, transparent tools like Global Feed that embrace openness as a guiding principle. As the demand for ethical AI grows, it’s clear which path will prevail.
Transparency isn’t just a buzzword; it’s a necessity. It’s the difference between tools that merely function and those that truly empower.
Choose Signal’s Global Feed
You can place your trust in tools that guard their secrets, or you can opt for solutions that place their trust in you by being transparent and forthright. The era of blind faith in “one-click magic” is over. It’s time to demand transparency. And with Global Feed, that demand is met honestly and upfront.
Choose transparency. Choose trust. Choose Global Feed.
Generative AI and Open-Source Intelligence: Evolving Together for Stronger Insights
Marrying Generative AI with Open-Source Intelligence: A New Era of Collaboration
Open-source intelligence (OSINT) plays a critical role in identifying risks and mitigating threats. However, as the sheer volume of data available continues to grow, the workload for analysts becomes increasingly unmanageable. Generative AI has emerged as a game-changing tool, not to replace the human element but to work alongside it, enhancing the efficiency and depth of OSINT efforts.
The Role of AI in OSINT
Generative AI transforms the OSINT process by automating repetitive tasks and delivering insights more efficiently. Tasks such as drafting reports, scanning social media, or analyzing large volumes of unstructured data can now be handled more effectively with AI tools. This allows analysts to redirect their focus toward deeper analytical thinking, rather than being bogged down by manual data aggregation.
Why Humans Are Still Essential
While AI is adept at processing data quickly, it lacks the ability to contextualize findings or understand the subtleties of human behavior. Analysts bring a depth of knowledge, critical thinking, and ethical oversight that machines cannot replicate.
For example, AI might flag a threatening social media post, but a human analyst would assess its credibility, motive, and broader implications. Human analysts are also better at triaging potentially threatening posts and deeper Behavioural Threat Assessments. Keeping a human in the loop ensures that the intelligence generated is not only accurate but also actionable.
Saving Time Through Automation
One of the most valuable contributions of AI is its ability to handle time-consuming tasks. These include scanning thousands of news articles, identifying patterns across multiple platforms, and summarizing dense reports. By taking on these labor-intensive activities, AI allows analysts to allocate their time to more complex tasks, such as horizon scanning, conducting behaviour threat assessments, and utilizing structured analytical techniques.
Enhanced Insights with Generative AI
AI tools are particularly effective in synthesizing large datasets to uncover trends and anomalies. For instance, generative AI can identify correlations in online chatter, highlight potential risks based on emerging patterns, and even generate hypothetical scenarios for organizations to consider. These capabilities empower analysts to make better-informed decisions, faster.
Navigating Ethical Challenges
The use of AI in OSINT also comes with ethical responsibilities. Ensuring the fairness and accuracy of AI-generated insights requires ongoing oversight from human analysts. This is particularly important in avoiding biases, respecting privacy, and ensuring compliance with legal standards. Human involvement provides the ethical compass needed to navigate these challenges effectively.
Generative AI is a Force Multiplier for Intelligence Analysts, Not a Replacement
Signal’s platform is designed to empower analysts by turning unstructured data into actionable intelligence, and generative AI enhances this mission by acting as a productivity multiplier. By automating tasks like data collation, summarization, and anomaly detection, AI streamlines workflows and frees analysts to focus on deeper analysis and decision-making. This integration doesn’t replace the human element—it amplifies it, allowing professionals to direct their expertise toward interpreting complex information and crafting strategic insights.
Generative AI within Signal’s platform also sparks innovation by surfacing hidden patterns, generating fresh perspectives, and suggesting alternative approaches. It operates as a tool in the hands of skilled analysts, whose judgment ensures accuracy and relevance. Signal’s commitment to blending advanced AI with human expertise creates a partnership where technology supports, rather than supplants, the critical role of analysts, driving more efficient and impactful intelligence work.
A Balanced Approach for the Future
Generative AI and OSINT are not competing forces but complementary tools.
Want to see Signal in action? Signal’s Global Feed delivers real-time insights from diverse, high-value sources across the globe, empowering analysts to stay ahead of emerging trends and threats.
Whether you’re tracking geopolitical developments, monitoring supply chain risks, or detecting hazards near your assets, Signal’s Global Feed provides the clarity and context you need to act decisively. Explore how Signal’s innovative platform is transforming open-source intelligence—learn more here.
The Crucial Role of Executive Protection in Safeguarding Leaders
Brian Thompson, the American CEO of UnitedHealthcare, was fatally shot in New York City while walking to an investors' meeting. The assailant ambushed him outside a hotel, firing multiple shots and hitting Thompson in the back and leg in what law enforcement are describing as a premeditated targeted attack.
The incident sent shockwaves through the global business community, and underscores the growing dangers faced by high-profile executives.
With increasing societal tensions and heightened visibility through media, CEOs and other leaders are becoming prime targets for threats ranging from physical harm to cyberattacks. This alarming reality highlights the essential need for professional executive protection services.
As a leader in this field, Signal provides tailored solutions to safeguard individuals and their families in an unpredictable world.
Rising Risks for Corporate Leaders
Wealth, decision-making power, and public recognition make executives attractive targets for people holding personal grievances or extremist beliefs seeking financial gain, revenge, or notoriety. Threats can manifest in multiple forms, including:
Physical Attacks: Executives often travel to unfamiliar locations, attend high-profile events, and interact with diverse individuals—all increasing their exposure to danger.
Cyber Threats: Digital profiles and personal data can be exploited for blackmail or identity theft.
Online Threats: Online death threats to VIPs can precede offline physical attacks.
Harassment: Cyberstalking, fixated individuals, and gender-based harassment can often be found online with aggressive language, extremely negative sentiment, dehumanizing rhetoric, and hate speech.
Reputation Risks: Public figures are under constant scrutiny, where even minor missteps can lead to severe reputational damage.
The killing of the UnitedHealthcare CEO serves as a sobering reminder that even those at the pinnacle of corporate power are not immune to these risks.
For example, another crucial aspect of reducing risk for executives is monitoring the broader societal response following an incident. In the aftermath of recent events, "wanted" posters targeting healthcare executives have appeared across New York City, accompanied by a surge of online commentary endorsing the violence. While these reactions may not constitute direct threats, they reflect a hostile climate that could escalate without warning.
What Is Executive Protection?
Executive protection encompasses a comprehensive suite of security measures designed to mitigate risks and ensure the safety of leaders and their families.
Core elements include:
Risk Assessment: Identifying potential vulnerabilities through robust evaluations.
Personal Security: Close protection officers trained to manage real-time threats.
Travel Security: Planning and monitoring travel itineraries to ensure safe passage.
Cybersecurity: Safeguarding personal and professional digital profiles.
Emergency Response: Rapid interventions to neutralize immediate dangers.
Why Signal is a Trusted Leader in Executive Protection
Signal is designed to equip security professionals with real-time data and actionable insights. These tools enhance the capabilities of dedicated security teams by enabling proactive threat detection and response, ensuring executives and organizations remain protected in an increasingly complex risk environment.
Real-Time Intelligence
Signal’s cutting-edge tools monitor and analyze publicly available information, delivering actionable insights to preempt potential risks. This proactive approach ensures executives stay one step ahead of threats.
Customized Insight
Recognizing that no two executives face identical risks, using Signal, Executive Protection teams can offer personalized protection plans customized to an executive’s requirements.
The Broader Implications of Executive Protection
Investing in executive protection has benefits that go beyond personal safety. It:
Preserves Business Continuity: Ensures leaders can focus on their responsibilities without fear.
Upholds Reputation: Prevents incidents that could harm the public image of both the executive and the organization.
Provides Peace of Mind: A secure environment fosters confidence and productivity.
Lessons from the UnitedHealthcare CEO’s Tragedy
The loss of a prominent leader reverberates throughout industries, highlighting the need for proactive safety measures. As corporate responsibilities grow more complex, so do the risks. Businesses must recognize that the safety of their leaders is not a luxury but a necessity.
Signal
Signal is an advanced intelligence platform designed to proactively identify and provide insight to help mitigate risks to high-profile individuals and organizations. By leveraging real-time data from social media, news outlets, the dark and deep web and other open-source intelligence channels, the Signal delivers actionable insights to enhance executive protection.
This system enables teams to anticipate threats, monitor potential vulnerabilities, and respond swiftly to incidents.
By incorporating Signal into their security protocols, organizations can ensure comprehensive situational awareness and improved safety for executives. Learn more about Signal and the Global Feed here.
Take Action Today
In an uncertain world, executive protection is no longer optional. Signal’s expertise ensures that corporate leaders and their families can live and work securely. The tragic event involving the UnitedHealthcare CEO serves as a stark reminder of what’s at stake. Don’t wait for a crisis to act—reach out to Signal today to build a robust security framework.
Learn more about Signal’s services at Signal Executive Protection.
Global Feed - Risk Identification and Mitigation
Every day, Global Feed detects and publishes over 6,000 real-time situation reports on incidents occurring worldwide that could be impacting your organization and personnel. Our proprietary system processes millions of data points, aggregating and analysing all relevant information about an incident, cross-referencing the information with trusted sources, to deliver timely, accurate, and comprehensive situation reports. Best of all, Global Feed is New Zealand owned and operated, ensuring that you have the best possible local coverage!
How Global Feed works
Global Feed provides real-time alerts for a wide range of incidents, including shootings, explosions, stabbings, traffic collisions, infrastructure collapses, cyber incidents, port closures, and power outages. The data feed also tracks natural disasters, outbreaks, hazardous material, fires, and extreme weather events. Furthermore, potential disruptions such as riots and strikes can also be monitored, ensuring that you are informed of hazards that are impacting your organization's safety, operations, and logistics on a global scale.
Global Feed features
Filter by incidents by category, location, keywords, confidence level, and date range.
Set-up email alerts based on any combination of filters, or trigger notifications based on geo-fence proximity to your assets.
Subscribe to regular tailored briefs to stay informed on key regional security trends and developments.
Example use cases
A major New Zealand company uses Global Feed to alert them to security incidents near their assets, or potentially disrupting or harming their supply chain, personal, or interests.
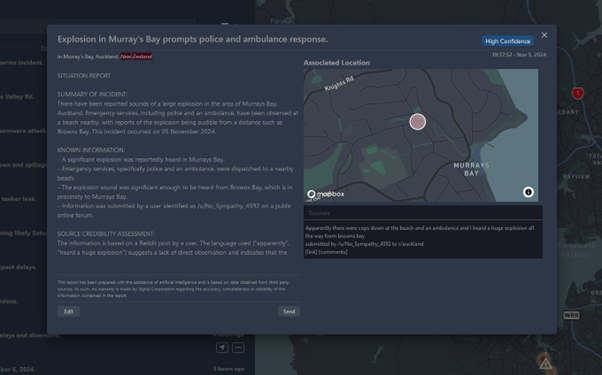
On Tuesday evening, the security manager receives an email alert that an explosion has occurred at Murray Bay within 2km of their CEO’s house. After reviewing the situation report, the manager knows that the explosion occurred at the beach nearby and that police/ambulance are on route – after a quick review, of the underlying source material, the manager proactively calls the CEO to apprise them of the situation and check that they are okay.
Over the weekend, the security manager receives an email alert that large demonstration will be occurring at Parliament across the road from their Wellington office. While not targeting their organisation, the manager is able to inform local staff of the potential disruption and to take necessary security precautions.
Screengrabs of Global Feed interface
How Global Feed can help your organisation
Do you need real-time alerts when a shooting or explosion occurs near one of your offices?
Would you like to be notified if your supply chain is disrupted by road closures, port strikes, or bridge collapses? Are you concerned natural disasters might disrupt your CEO’s travel plans?
Do you want to stay ahead of major incidents that could impacting your employee’s safety?
If you answered yes to any of these, it’s time to consider Global Feed. Stay informed, stay ahead, and protect your assets with our comprehensive, real-time incident detection.
The Role of AI in OSINT: Introducing New Briefer Tool
Launching Briefer into Signal’s security solution is an exciting next step for the platform, and it highlights the budding potential of where AI is headed and where it is today.
Open source intelligence (OSINT) has transformed in recent years, following the explosion of data and the introduction of artificial intelligence (AI), effectively hallmarking a new era of security support solutions.
AI-driven OSINT tools excel in collecting and analysing publicly available information from diverse online sources. We’re excited to be at the forefront of this new era, announcing a new feature within our latest version of Signal, Briefer, designed to reduce repetitive tasks for security teams, streamline processes and make hunting out threats faster and easier.
Artificial intelligence and open source, a powerful match
There is a growing demand for solutions that improve efficiency and enable teams to quickly track and research vast data across the web and social media. Top players in the market have been identified as those that can provide expert analysis and interpretation of the data they collect, identifying patterns and trends, and sifting genuine threats from noise.
In addition, while AI and machine learning has been used in security processes for more than a decade, with the rise of generative AI and tools such as ChatGPT, AI has reached a new level of usability of everyday security staff, with clever and widely functional use cases showcasing the power of the technology.
In our digital age, AI models are now able to meet the scale of the open data landscape, so instead of an insurmountable challenge it becomes a goldmine of information to be analysed. As a result, security teams are greatly empowered, and the business and its people benefit from being one step ahead of threats.
Breaking down the role of AI in OSINT, and introducing Briefer
As highlighted by Oxford Internet Institute, “AI can also assist the analysis phase of the OSINT cycle, generating valuable intelligence based on pre-trained models and thus countering the information overload problem faced by intelligence analysts.”
With the help of AI, pages upon pages of public web information can be scoured, as the intelligent solution sifts through mentions, news and opinions to flag potential threats, sharing a selection of alerts with a human team.
In addition, in the case of Signal’s new tool Briefer, reporting becomes simplified and more consistent. The AI algorithm enables teams to select various components for their report, and create it instantly for key stakeholders.
At its core, AI is improving OSINT in three ways. That is, improving data collection, developing data analysis, and generating actionable insights. This includes assisting in the prioritisation of data, correlating relevant information, reviewing raw information, and deriving relevant insights with key tags so human analysts can sift through alerts.
As we are already seeing, emerging technologies, including AI, don’t replace the role of the security team, but have the potential to greatly enhance it, saving time throughout the whole process, from hunting for threats to reporting on potential disturbances.
A new phase of security intelligence
Launching Briefer into Signal’s security solution is an exciting next step for the platform, and it highlights the budding potential of where AI is headed and where it is today.
It also shows how AI-enhanced OSINT can become an integral security resource, not to replace human analysts, but provide a foundation of efficiency and insight so they can focus more time and attention on securing the business and its people.
Review our latest product updates and book in for a free demo.
Threat intelligence climbs into the billions - and a special 10-year anniversary update
The need for threat intelligence solutions continues to rise as security leaders need to sift threats from noise and increasingly safeguard their organisation and people from online threats.
The need for threat intelligence solutions continues to rise as security leaders need to sift threats from noise and increasingly safeguard their organisation and people from online threats.
At Signal, after a decade providing leading threat intelligence solutions to a wide range of industries, we’ve seen the genuine impact digital risk management can offer in supporting the safety, security, and operational resilience of organizations.
Whether in banking, healthcare, insurance, utilities, manufacturing or entertainment, being able to monitor online data, including the dark web, can go a long way in identifying any threats to your people or daily operations, and respond quickly as needed. As technology advances so can our means of stopping threats in their tracks.
Threat intelligence market as booming market - and we can see why
In 2022, the global threat intelligence market Fortune Business Insights size is expected to experience a boom, reaching US$18.11 billion (NZ$30.6 billion).
During this forecast period, the Asia Pacific market is expected to grow significantly as security leaders seek to enhance their resilience.
Our threat environment is more complex and dynamic than ever before – rising geo-political tensions, devastating natural disasters, cyber-attacks, and the growing threat posed by violent extremism and a multitude of other drivers presents security leaders with significant challenges. Particularly amidst growing talent and skill shortages leaving security teams time poor and burnt out.
On a positive note, artificial intelligence (AI) is greatly advancing organisational resilience, particularly through centralising threat intelligence. In fact, recent market research has found that 69% of enterprises see AI as a necessary investment for responding to cyber-attacks, and 51% of executives see cyber threat detection as the use primary case for AI.
With effective threat intelligence that leverages emerging technologies, businesses can make use of one platform to monitor threat data from a wide array of data sources and formats. They can aggregate all relevant data from across the web and make it easily understandable, vastly improving the ability to mitigate risk.
Responding to a growing need - introducing Signal Version 4
Over our decade in the threat intelligence industry, we’ve always been user-led. As part of our commitment to Signal users, we’ve placed the majority of our focus and resources into providing updates and solutions to our platform that are in direct response to how people are using our services and tools.
Signal Version 4 is a culmination of months of deep-diving into how we can best improve and advance our services to cater for our modern, digital, and increasingly AI-driven business world.
This is a major update to the existing service, and also provides a new foundation to allow us to build out our powerful AI functionality, along with ongoing full-service updates. Behind the scenes we’ve been building, testing, reiterating and smoothing out both the underlying solution infrastructure and the topline view, to ensure utmost resiliency and usability.
While we’re excited for our users, new and existing, to try it out themselves, we’re most excited about our AI additions, improved user interface, data visualisation capability, customisable dashboards, and global event detection and alerting.
While security teams are up against notable challenges, with clever, user-led threat intelligence tooling we can prepare for the worst, catch risks that arise, and respond in kind.
Review the latest updates and book in for a free demo.