How can 4chan be Used as a Data Source for Security Intelligence?
4chan is just one of the data sources you can monitor using Signal. You can find conversations by alt-right groups, threats of violence against a person, organization or group, and more, which makes it a valuable data source for security professionals.
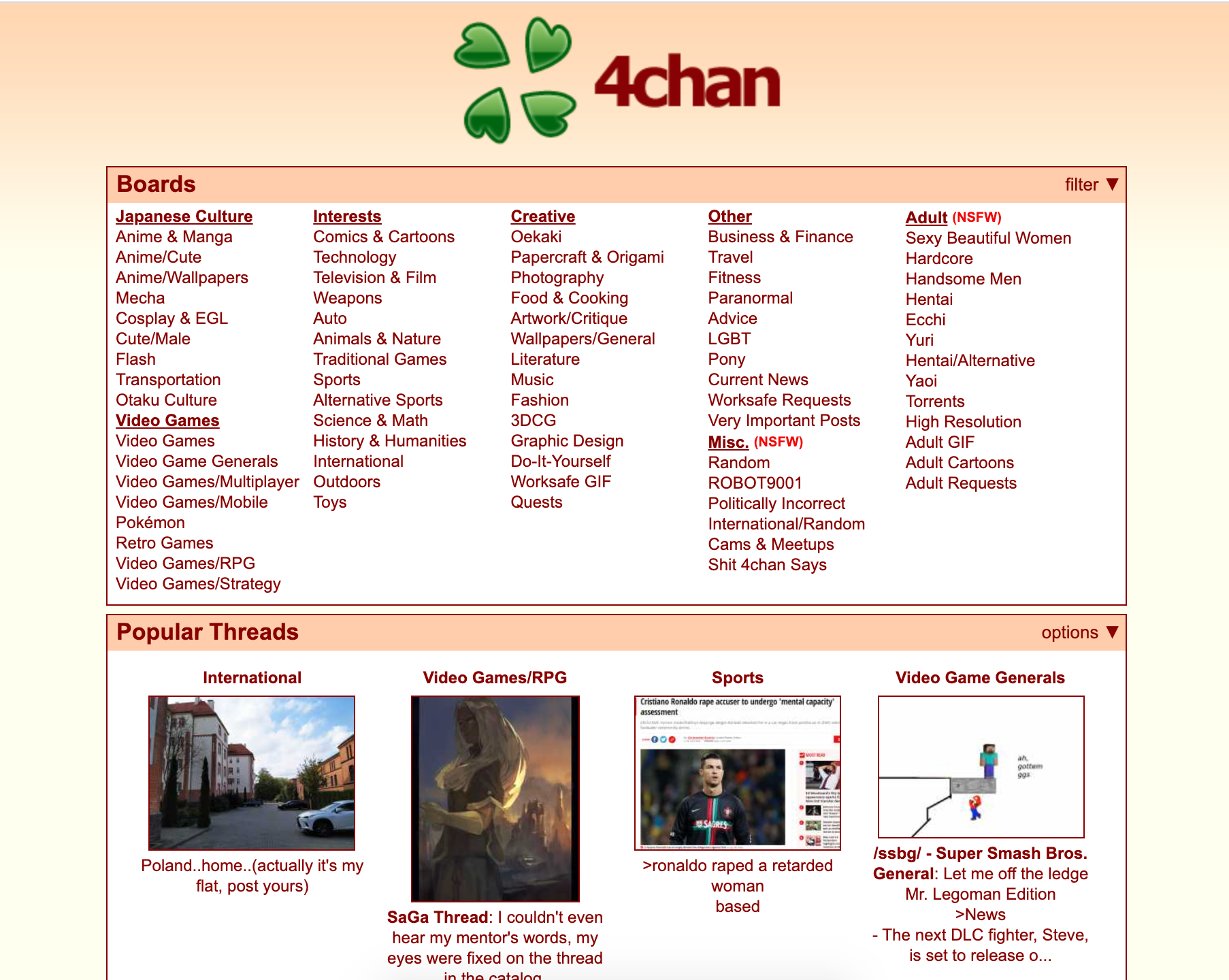
What is 4chan?
4chan is one of the largest English language based image boards on the open web. They have over 900k new posts per day and some 27 million active monthly users.
What makes it a unique social platform is that users can choose to remain anonymous. They don’t even need to create an account to access and engage with content on the platform. As an added security measures, posts time-out after a period so they can’t, unless found and archived by an independent data gathering source, be checked and referenced by security teams, users, or law enforcement at later date.
There is a wide range of topics hosted on the platform, from Japanese culture, to politics, to adult content. Because of the anonymity allowed, as well as a very limited moderation by the site owners, 4chan has a large amount of illicit content and activity. This activity includes cyberbullying, child pornography, harassment, violent threats, racism and extremist ideologies.
Despite this, it’s important to note that there is nothing inherently bad about the platform, just as there is nothing inherently bad about the dark web, and many of the users use it for legitimate purposes such as for its original intent which is the exploration and discussion of the Japanese film and television animation style, anime. In fact, like Reddit, many influential memes have originated from the platform such as ‘lolcats’ and ‘chocolate rain’. As such it has historically been an important driving force behind the development of internet culture.
Bottom line: 4chan is a forum, the original purpose was for the discussion of anime and Japanese culture. It’s a forum where users don’t need to have an account or sign up with a name, there is little moderation, and posts are deleted from the server after a period, as such there are few consequences. With this format, people can and do say just about anything on the platform.
How can 4chan benefit your organization as a data source?
The anonymity offered by the channel means users feel comfortable talking openly and they do so around a wide range of subject matters and people. For example, under the political forum /pol/ you can find examples of alt-right groups, threats of violence against a person, organization or group, and racist behaviour.
The range of topics discussed and the freedom with which individuals and groups openly discuss them can give security teams and law enforcement an idea of emerging trends as well as be one of the first places that death threats or threats of violence against individuals and organizations can be found. In the past, terrorist manifestos have also been posted on the channel. These discussions can indicate when an event is going to evolve into a tangible threat and give security teams a heads up to prepare and mitigate the potential threat.
Additionally, there are groups and individuals on the channel, such as the members of Anonymous who have turned their online attention, for right or wrong, to intelligence gathering on people and organizations. Often, 4chan is one of the first places they share their findings. For example, they might uncover and share personal details about a CEO such as their address, medical records and details of their family.
Why use Signal for monitoring 4chan?
One of the key problems with any form of online intelligence reconnaissance is the quantities of data you need to assess to get even the smallest tidbits of potentially useful information. 4chan has this problem in spades with over 3.5 billion posts. And these posts are transient, with the more R rated the post being the shorter it’s existence. This means relevant security intelligence on the 4chan platform might only be public for a couple of days. To gain real insights into the channel you need to be constantly and efficiently monitoring with real-time alerts.
4chan is just one of the data sources you can monitor using Signal though. You can simultaneously monitor the open, deep, and dark web including forums like Reddit and chatrooms like Telegram. Our system allows you to create tailored keyword-driven searches with boolean logic which is assisted by our machine learning and language processing AI to efficiently gain intel on hyper-relevant, new and emerging threats.
The Role of Threat Intelligence and Cybersecurity in Retail
The rise of e-commerce and the adoption of digital technologies has opened up a number of new security risks for the retail industry. Hackers who manage to take advantage of any of these attack vectors can do a lot of damage to both a companies bottom line and reputation. Which is why it's more important than ever for businesses to employ the right tools to protect their people, data, and assets.
Retail is the fourth most targeted industry by cyber-criminals. It is the same technologies that have created new potential growth opportunities for these businesses which has simultaneously opened up new and evolving attack vectors for both cyber-criminals and physical attacks.
Use of the cloud, IoT (Internet of Things) and global expansion increases potential risks exponentially, as these threats are no longer constrained by location or borders. Organisations need to secure customer data, protect executives, manage travel, predict physical threats to assets, and prevent cyber-attacks. All of these threats could come from a range of possible sources involving a plethora of evolving methods, from anywhere in the world.
Digital and In-Store Locations Are Both Valuable Targets
Retailers deal with large numbers of people. As such, their databases necessarily contain vast amounts of data which could be valuable to hackers. This includes but isn’t limited to personally identifiable information (PII) for customers, employees and even executives. Vulnerable PII which contains financial information is highly valuable and the most obvious of targets for hackers, however, even non-sensitive data can be a hugely profitable attack vector for cyber-criminals when used correctly. This is shown by the frequent sales of login credentials on the dark web.
Additional avenues of attack include mobile retailer apps, customer-facing devices in retail locations, and IoT product offerings. These new technologies are continuously assessed by cybercriminals for potentially exploitable weaknesses and can often be found mentioned in online discussion forums. Because of this, public-facing social media data, as well as data collected off the dark web, is more valuable than ever in detecting threats.
Social media, as well as anonymous forums on deep and dark websites, are used to discuss or advertise criminal strategies like shoplifting, POS fraud, and counterfeiting. Public-facing social media data is more relevant than ever for detecting sentiment, executive threats, and critical events like active shooters in or around retail locations.
The Heavy Cost of Threats for Retailers
The cost associated with the risks outlined in this article are huge. Retail inventory loss incurred by shoplifting or fraud costs the industry an estimated $50 billion a year. The average cost of a data breach, according to a 2018 Ponemon Institute report, is USD $3.86 million. And these are just the measurable costs. The long lasting effects that comes with the reputational damage and global brand erosion that coincides with a data breach that exposes customer or executive data is also a highly valid concern.
This information points to the importance and necessity for an effective data discovery and analysis programme to be employed by companies to effectively secure organisations in the retail industry. Security teams are burdened with a seemingly impossible task of processing an ever-increasing and varied amount of threat data to separate the noise from the real threats to contextualise that data into actionable insights. This industry needs tools that automate and accelerate data analysis to enable effective threat monitoring and prediction.
- 50% of retailers have experienced a data breach.
- 84% plan to increase IT security spending.
- 85% of retail IT security professionals said their organisation used cloud storage for sensitive data.
The Importance of Cybersecurity in Retail
The rise of e-commerce and the adoption of digital technologies means that retailers now hold vastly more data on their customers than ever before. Most major outlets currently have online stores and it’s expected that online sales will outstrip high street sales within the decade. Gaining access to customer accounts can give access to PII and even bank details. Hackers who manage to obtain this customer data will either use this data themselves or more likely sell it on the dark web.
One of the popular methods that this data is used for is an approach called credential stuffing. This attack works because many customers use the same login credentials across many different sites. Hackers will take these credentials and make multiple automated login attempts across an array of websites. One team of security analysts found that 90% of retail login attempts were from hackers attempting to access other people’s accounts in this way.
Another common attack vector is payment processes. Retailers are embracing technology to make it as easy as possible for customers to purchase through their online stores, however, if security standards aren’t advanced alongside these payment processes then they leave vulnerabilities to fraudulent activity.
A final key cybersecurity vulnerability for retailers is the staff. Often retailers hire young and inexperienced staff, most of whom have had little if any cybersecurity training. This leaves them vulnerable to common ‘social engineering’ attacks such as ‘phishing’. For example, a hacker might contact a staff member directly and trick them into installing malware onto a company device or attempt to get them to provide sensitive information by pretending they are someone that they aren’t.
Additional Threat Vectors for the Retail Industry
A few examples of additional threat vectors that the retail industry need to pay careful attention to include:
Gift card cloning
In a 2018 report security firm Flashpoint identified found hundreds of discussions of "cracked" gift cards on criminal web forums.
There are several strategies to hack gift cards. One example is by predicting the gift card numbers, which when combined with a brute force attack, means hackers can identify activated cards and the amounts on them. Another method involves creating clone cards of inactive gift cards and then when they are activated using the credit before the rightful owner has a chance.
Whichever method they choose it’s often the retailer that’s left picking up the tab.
Executive and employee threats
As with any industry, staff may be targeted, not just for phishing attacks or fraud but for physical attacks by disgruntled customers or even terrorists.
Threats to physical locations
From active shooter attacks to terrorist assaults physical locations, especially those where members of the public can come and go freely, are high-risk locations.
By utilising the right technology companies can identify threats early and mitigate the potential damage by forming an effective response based on real-time data fast.
What modern security means for modern retail
Criminals can leverage the web to commit both physical (such as in-store theft), as well as cyber-attacks (such as phishing or gift card cloning). This leaves retailers operating in a unique threat landscape with a broad array of potential attack vectors.
There are three levels that modern retailers should consider to ensure a complete and effective security, both in-store and online. First, at the highest level, training and information need to be gathered for both their security teams, both also disseminated to employees across the organisation so that everyone is aware of the threats and how to avoid them.
The next level is to only work with secure third-party providers. Companies that take security seriously and when it comes to building defences against cybercrime have strong records. These businesses, such as connected devices, cloud storage or payment portal providers form a crux of any companies security.
Finally, the security team need to be enabled with the right tools for the job at hand. Signal OSINT software enables security teams to scan a vast number of open, surface, and dark web channels and sources to gain real-time data on emerging threats. Our sentiment analysis, custom filters and advanced alerting means security teams can be notified instantly on threats as they are emerging. Whether it’s customer data for sale online, or an active shooter situation in-store, security teams can quickly assess and respond to mitigate risks and damages.