Securing the Supply Chain: The Role of OSINT in Logistics
Open Source Intelligence (OSINT) is an integral tool for both security teams and supply chain managers to enable them to gain clear oversight of potential disruptions across the supply chain and implement timely responses.
Supply chain operations can be vast. While globalization and digital technologies are making the world a smaller place in many ways, they also increase the number of potential vulnerabilities that security teams and supply chain managers must monitor. Current threats to the logistics sector include climate and weather events, piracy, terrorism, DDoS attacks, malware and data breaches.
The range of potential threats is exacerbated by the vulnerabilities of the supply chain and the sheer size and scope of the operations involved. For example, around 90% of the entirety of global trade flows through only 39 bottleneck regions. An effective attack on any of these 39 traffic-heavy logistics hubs would have far-reaching consequences impacting billions of dollars of trade.
One example is the Hong Kong-Shenzhen freight cluster, a critical gateway for global manufacturing and trade, through which tens of millions of tonnes of container and air freight move annually. Additionally, there are a number of geographic chokepoints, such as the Panama Canal and the Strait of Malacca.
It is no longer merely the threat of attacks to these areas, which could halt a vast amount of freight. Incidents, such as the grounding of the Ever Given in the Suez Canal in 2021 and the drought that restricted movement through the Panama Canal in 2023-24, demonstrate that these geographic chokepoints are increasingly vulnerable.
If this wasn’t enough, digitization has increased the number of threats that logistics companies need to consider. This increase in vulnerability needs to be addressed through effective security measures, such as real-time data collection using Open Source Intelligence (OSINT) software.
How can transport and logistics companies secure their supply chains?
Ensuring secure passage
One of the key concerns – and one of the oldest – that logistics and transport companies have to contend with, is tangible and physical security threats; terrorism and piracy being the obvious examples. The rise in extreme weather events, such as hurricanes and droughts, also places pressure on logistics routes. Organizations need real-time information to carefully and continuously assess the threat level, implications and risks surrounding these physical security concerns.
These analyses help organizations to develop mitigation strategies. They also help to establish contingency plans for worst-case scenarios. Organizations need to be able to adapt and respond quickly to events as risk levels change. Supply chain managers across all industries need to consider higher transportation costs, longer travel times and potential issues in meeting schedules when alternative transportation routes are used.
These strategies depend on continuous visibility of current and emerging threats. Without this response, planning is compromised. Being caught unawares could have far-reaching and even devastating consequences. And, in some cases, business models based on time-critical deliveries may be squeezed out of the market.
Keeping cyberspace safe
Cybersecurity is a concern that should be receiving increasing attention as cybercriminals continue to evolve their tradecraft.
In 2017, a cyberattack cost shipping giant Maersk upwards of US$300 million. A vicious malware called NotPetya took down Maersk’s IT systems. Maersk was handling roughly one container ship into port every 15 minutes. So, it's easy to imagine the logistical nightmare that ensued as the company was forced to turn to manual processes to keep things moving.
The Russian military developed NotPetya to target businesses in Ukraine – but the malware quickly got out of hand. Soon, it was spreading around the world, taking down networks and causing billions of dollars in damage and lost revenue. In this scenario, Maersk was simply collateral damage.
More recently, Expeditors International were affected by a cyberattack that forced them to shut down their operating systems, disrupting their services for more than three weeks. Expeditors later revealed the attack had cost them $60 million in lost revenue, investigation and remediation.
Transportation is already heavily reliant on Information Communication Technology (ICT), with virtual threats growing in frequency and complexity. For this reason, cyber threats are an increasing concern across multiple industries. Additionally, for transportation and logistics, cyberattacks designed to induce physical damage are an increasingly common attack vector.
OSINT software for a more secure future
Some organizations operate with hundreds of individual suppliers. If any supplier is disrupted, consequences across the supply chain could be costly. Expeditors International and Maersk are just two examples of this.
Investing in live threat detection doesn’t just reduce risk; it also keeps operations running smoothly and predictably. When it comes to security and supply chain management, it’s especially important to look at future scenarios and manage security proactively. Reacting to crisis situations is not enough. Companies must find the right combination of preventive and reactive measures to achieve the optimal level of supply chain security.
Executives should also keep an eye on so-called wildcard events. That means examining the potential financial impact, the relative vulnerability of their business model, and their company’s ability to respond to low-probability, high-impact events.
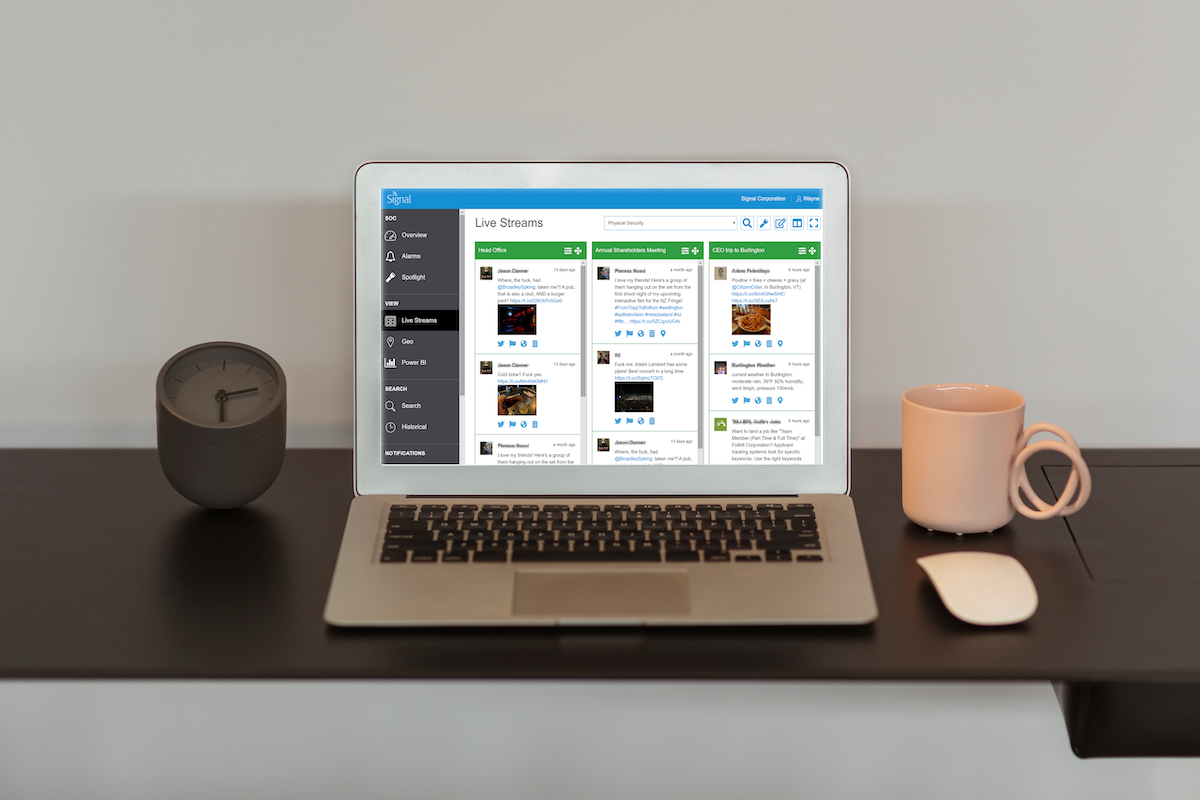
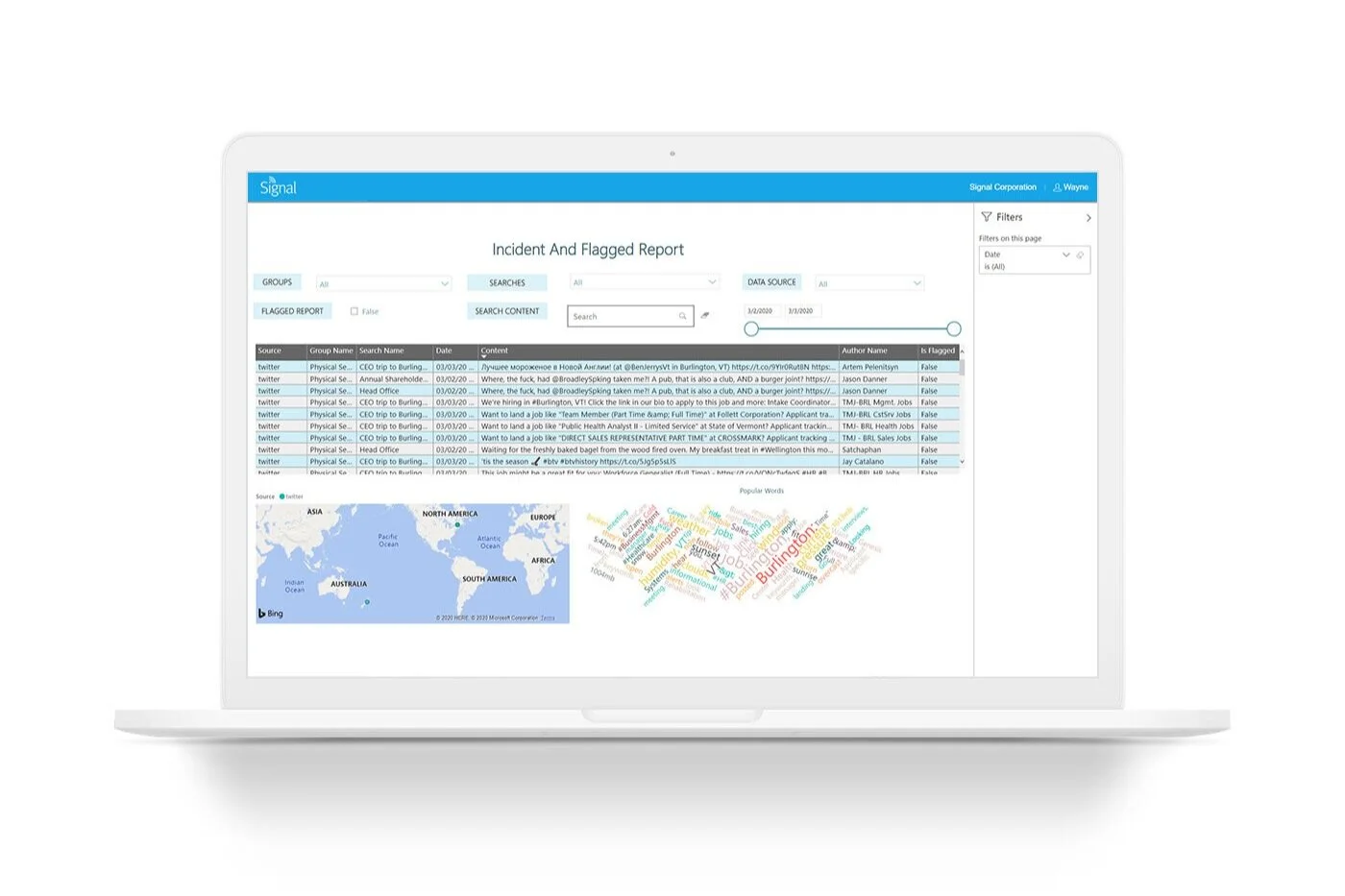
As supply chain threats multiply, staying ahead of the intelligence flood becomes more difficult. Signal’s tools cut through the noise by using AI to perform tasks, such as triaging alerts and providing contextual SITREPs for possible threats. This sort of practical application of AI creates efficiencies within security teams, without compromising the crucial situational awareness needed to keep logistics lines open.
How Signal is already helping secure logistics supply chains
Signal alerts a customer to a supplier’s merger. They can find new suppliers in a timely fashion, preventing disruption and revenue loss.
Signal provides data on severe weather warnings that affect multiple suppliers and disrupt transportation routes.
Confidential data is found for sale on the dark web, allowing the organization to act quickly for threat mitigation.
How Monitoring Current Events Like the 2020 US Election Can Increase Organizational Security
Tensions around the US election are high for both ends of the political spectrum. There has been an increase in polarization and militarization and many Signal customers have expressed concern.
There are numerous threats that could evolve to seriously impact an organization, from natural disasters, to acts of terror, to targeted attacks on executives. Currently though, tensions around the US election are high on both ends of the political spectrum. There has been an increase in polarization of political views and even militarization of the public in recent months, and many Signal customers have expressed concern.
For many American’s this is seen as the most important election of their lives so far. Fears of voter fraud and voter suppression are rife, which is reflected by an unprecedented number of early votes being cast with more than 90 million votes already cast a week before the election, more than two-thirds of all the votes cast in 2016.
This, paired with a deadly pandemic and a summer of protests, many of which became violent, and one can see the potential for civil unrest around a contentious presidency. To mitigate this risk organizations need relevant intelligence as events unfold to ensure they take the necessary precautions to protect their employees and assets.
As such, we have created advanced tools to enable Organizations to be alerted as early as possible to issues and current events, such as the Election, where the possible fallout could have an impact on their employees and assets.
Monitoring Election Threats in Real-Time Using Signal OSINT
Using Signal security teams can learn of events as they are happening or even before they happen, allowing effective response plans to be enacted, effectively neutralising potential threats.
To do this users can create custom searches using Boolean Logic to filter intel from key web sources such as social media, the open web, and the dark web. Intel from these sources often acts as an early indicator alerting Signal customer to potential issues in real-time. The data can also be reviewed by our emotional analysis solution for increased data analysis efficiency.
Signal has real-time SMS and email alerting for high-risk threats so that companies can maximise available response time. Once alerted to potential risks the security team can form a final judgement on the threat level and decide whether action needs to be taken.
Final Words on Threat Monitoring with Signal
Threat monitoring isn’t just for events such as a contentious election. COVID-19, earthquakes, storms and other extreme weather events, and even threats of violence against specific executives, can all affect an organization. Signal OSINT software enables security teams to scan a vast number of surface, deep, and dark web channels and sources to gain real-time data on a broad array of emerging threats.
Anonymous social media forums like 4chan or dark web forums are often where threat actors go to communicate and organize. And social media is often where you can learn of current events as they unfold. So whether it’s customer data for sale online, or an active shooter situation in-store, security teams armed with OSINT can quickly assess and respond appropriately to mitigate risks and damages.
Only when an organisation has a complete picture that incorporates the variety of potential risks and has invested in specific responses and contingency plans can it adapt as needed to mitigate the impact of extreme events.
Operational Awareness for Improved Supply Chain Risk Management
Supply chain managers need accurate real-time intelligence over the entirety of operations to enable them to react to supply chain risks promptly and mitigate potential damages.
A supply chain risk can vary broadly, from volatile global politics to natural disasters, from terrorism to DDoS attacks or data breaches. A disruption anywhere along the supply chain could have serious ramifications for business continuity potentially costing an organisation millions. Additionally, the size and scale of operations means that there are often numerous vulnerabilities.
Open Source Intelligence (OSINT) is an invaluable tool for both security teams and supply chain managers. It allows them to gain oversight over often vast and complex supply chains, monitor risks and threats, and gather real-time data that is essential for coordinating an effective response.
Many supply chain risks and threats are in association with fears around break downs within logistics operations or supplier disruptions. Additional concerns also relate to financial and legal exposures, uneven market demand for product, mounting competition, and natural disasters.
Protecting Business Continuity from Supply Chain Risks
Even as product complexity expands supply chains continue to stretch into developing countries where labour and natural resources are plenty, but the infrastructure is undeveloped or insufficient. Meanwhile, advanced planning and sourcing practices which aim to maximize efficiency and minimize costs, stretch operations to a point of fragility.
Any disruption can result in organizations and consumers worldwide feeling the impact via loss of suppliers, delayed or destroyed goods, product release delays, and ultimately, customer dissatisfaction and brand damage.
To mitigate the damage of potential threats, both physical and cyber, specific resources need to be designated with the goal of maintaining business continuity in the face of disruptions. One of the most essential resources for security teams and supply chain managers alike is relevant insights and intelligence to assist in assessing potential supply pitfalls.
Key Supply Chain Disruptions to Monitor with OSINT
Traffic
Even something as seemingly mundane as traffic can cause havoc with supply chain management as supply chains are heavily reliant on good transportation networks. Security professionals and supply chain managers need to know fast if key transportation networks are endangered.
For example, if a freight hub such as Hong Kong International Airport which sees nearly 3.7 million tons of freight through its gates each year were to encounter a serious disruption the ramifications would be far reaching. It’s not just physical disruptions though that teams need to monitor as cyber attacks can have equally far-reaching consequences.
Weather
It’s hard to predict where and when a tornado, hurricane, severe thunderstorm, or debilitating snowstorm will hit. However, in certain parts of the world such as Southeast Asia, these severe weather events occur more seasonally.
For example, in 2015, the top 4 typhoon events in Southeast Asia caused an aggregate of over $33.5B in damages, more than 138 days of recovery time, and impacted nearly 7,000 supplier sites. In response to the increased risk of extreme weather events organizations must confront the complexity of their operations and improve visibility to go beyond just their immediate vendors.
Only when an organisation has a complete picture that incorporates the variety of potential risks and has invested in specific responses and contingency plans can it adapt as needed to mitigate the impact of extreme weather events and maintain strength in the marketplace.
Mergers and acquisitions
A single organisation may work with hundreds of independent suppliers from all over the globe. It’s important to have clear oversight of their operational capabilities as well as retaining an awareness of how global events such as extreme weather or in this scenario a merger or acquisition might affect their output.
What organisations cannot do is assume the best case scenario. Like other threats mentioned in this article, this supply chain risk is exacerbated by the scope of the operation. A single delayed part, for example, could bring assembly lines to a halt causing a build-up of undelivered orders ultimately resulting in dissatisfied customers and a long-term loss of revenue.
With potentially hundreds of suppliers and thousands of parts it’s not practical to maintain frequent communications with every single supplier, nor is it possible to manually oversee the entirety of the supply chain.
Fire and the Unexpected Physical Disruptions
While some events can be predicted and planned against, others can’t. A fire in a warehouse for example. Or as we have seen recently COVID-19 which has caused havoc across supply lines with factories either temporarily shutting down or reducing the scale of their operations with limited workforces.
Such unexpected crises can have a big impact causing costly delays. Organisations need up to date and real-time information on all their respective suppliers if they are to react fast and mitigate the potential financial impact of these supply chain risks.
Cyber Threats
There are multiple threat vectors that cyber attackers could target. And as operations get more complex and they focus increasingly on utilising technology for increased efficiency, these vulnerabilities become progressively more concerning. Attacks could take the form of anything from customer data breach, to leaked information pertaining to sensitive company data or even as in the case of Maersk, a rogue malware completely taking down an organisations IT systems.
Related: Securing the Supply Chain: The Role of OSINT in Logistics
Conclusion
New demands and pressures are constantly stretching supply chains and forcing supply chain managers and security teams to adapt. The stakes are high and security is a critical factor. Major concerns such as an unstable global economy, aggressive market competition, extreme weather conditions, demand volatility, and production failures place revenue growth, reputation and overall business operations at great risk.
Understanding the nature of potential vulnerabilities and keeping current on disturbances that can impact processes can help teams better handle and mitigate problems related to global supplier concerns, brand protection, and financial risks.
Open Source Intelligence monitoring solutions like Signal enables teams to gain a clear oversight of the entirety of their logistical operations. This means they have details of potential disruptions or cyber-attacks before, or as, they are happening, allowing security teams and supply chain managers to implement their contingency plans in a timely fashion and prevent unnecessary financial losses.
Fighting Disinformation: How to Detect Bots and Determine Fake News
In our increasingly digital world the proliferation of disinformation forms a serious threat to organizations. To combat misinformation companies need the right tools and information.
In an increasingly digital world, there is scope for fake news publishers to make a huge social impact as well as large profits through the spread of disinformation. Accordingly, this is a problem that has and will continue to grow. The spread is compounded by our very human natures which compel us to engage with inflammatory content and often share before we’ve had time to fact-check and verify.
The spread of disinformation is problematic on a number of levels, it can impact a brands image, spread harmful or misleading medical information - as we’ve seen throughout COVID-19, or even undermine democracy itself as was seen in the 2016 US elections. Ultimately, to combat misinformation organizations need to be equipped with the right tools and understand both what they’re looking for, and the reasons for spreading misinformation.
The High Cost of Fake News
There are serious potential ramifications for the unchecked proliferation of misinformation which can impact both B2C and B2B organizations. For example, a competitor or disgruntled customer or employee could hire or create a fake news publisher to damage your brand image for purposes of revenge or to gain a competitive market advantage.
These adversarial news generation sites could easily generate a huge amount of very believable content, syndicate across a number of channels, and promote heavily through social media, potentially through the use of bots. Overwhelmed companies would face a significant challenge when developing a response to counteract these examples of bad “press” and it would be necessary for those targeted organizations to have real-time actionable data at their fingertips.
How do you Spot a Bot?
Anonymity
Real people sharing real stories will have full accounts, normally with a photo of themselves. These people will have friends, followers, family and likely engage largely with their friends content. The opposite is fairly true for bots. Bots, by their very nature don’t have identities which often results in bot accounts appearing to have a highly anonymous approach.
This could be evidenced in the lack of information they share, or perhaps they use a generic profile picture like a well-known landmark.
Activity
The frequency of their postings as well as how successful those posts are are good indicators of a bot. For example, you might come across an account with only one post and no followers yet that post has thousands of shares.
Content
The people that create bots have an agenda. Whether that’s to drive traffic to a website, generate income, spread political disinformation, etc. Whatever, their reason, the bots will be used to achieve it which means all their posts will have a common theme such as inflammatory political context.
Stolen photo
It’s not uncommon for bots to steal profile pictures. A quick test can be running their profile picture through Google image finder to find the real owner of the image.
Related: Responding to Global Crises like COVID-19 with Increased Situational Awareness
Things might appear real at a glance, but prove to be fake on closer inspection..
A quick checklist for botnet detection
Bot accounts used in one network or campaign usually have several of the below listed features in common:
Multiple accounts with similar names or handles;
Accounts were created on the same date;
Each account is posting to the same sites, or even the exact same links;
The same phrasing or grammatical error appears across each accounts;
They all follow each other and/ or share each other posts;
They use the same tool for link shortening;
The bios have similarities;
Profile pictures are generic or identifiably not them (easily searchable through Google).
Obviously, just because some accounts have similarities doesn’t mean they are all bots, however, it should certainly raise some eyebrows in suspicion especially if you have four or five accounts with several of these signs.
Fake Accounts vs. Account Takeovers
We outline above a few of the tell-tale signs of a bot. There is an additional tactic that is commonly used to amplify the distribution of fake or inflammatory content and this is through an account takeover.
For this approach botnet operators perform credential stuffing attacks on social media accounts and then use the accounts they gain access to, to share information through direct messaging or by sharing content. Additionally, a compromised account could theoretically mean sensitive information is exposed and executives or organizations as a whole could suffer reputational damage or financial loss.
Standard security protocols, such as having unique passwords for all your online accounts, should help individuals avoid becoming victims of these tactics.
The Importance of Verifying Information
The best way to check the accuracy of a source is to check it against another source.
However, this does raise another question. What if those other sources, those source which are supposed to independently verify the truth are working with the information source you’re fact-checking. Or what if the facts in the source are. largely correct but the story is spun to support one side of an argument. This might ring with scepticism and conspiracy, however, it is a point worth making, with whom do you place your faith and at what point do you stop questioning the validity of information?
Identifying Click-bait
Click-bait titles are purposefully crafted to evoke a powerful response from the readers. The reason for this is it encourages people to share the post, often without even reading the text. Less reputable news sites are occasionally guilty of this tactic, twisting the truth in their titles to get a response and increase their reach. However, it is also a tactic employed by botnet operators to maximise the reach of fake news. Signs that this might be the case are as follows:
Does it evoke a strong emotional reaction?
Is the story utterly ridiculous - or does it perfectly confirm your beliefs?
Are you going to spend money because of it?
Does it make you want to share it?
What’s the Bigger Context
Understanding the context behind a piece of news can help you determine how much, if any, of the story is true as well as lead you to a better understanding of what the publishers end goal is.
Who’s providing the information?
What’s the scale of the story?
If there’s an “outrage,” are people actually upset?
How do different news outlets present the same story?
Understand their Angle
Just because something is misleading or even incorrect doesn’t mean it’s without use especially in a security context. In fact, understanding the reason behind the content might give insight into potentially harmful tactics targeting your organization and better allow you to create an effective response.
When determining what their angle is ask the following questions:
Are important facts getting left out or distorted?
What’s the larger narrative?
What if you are actually wrong? Your previous opinion on a subject might have been formed by a different piece of fake news.
Why did they share this story?
Determining Truth from Fiction Online with Signal OSINT
How companies utilize technology and adapt to the shifting threat landscape will determine how effectively they are able to mitigate the threat of disinformation.
Signal enables organizations to monitor and manage large amounts of data from a plethora of different data sources across the surface, deep, and dark web. This, paired with advanced filters and boolean logic means that security teams are empowered to identify disinformation, discover patterns and botnets, and practically respond to these potential and evolving threats.
Additionally, Signal enables security teams to detect data leaks. This data may be used in credential stuffing attacks and poses a severe security risk. Identifying data leaks early is essential for mitigating the threat of credential stuffing and in this case preventing harmful misinformation from being spread through or by an organizations workforce.
Combining Human Analysts, AI, and Automation for Fast Threat Intelligence
Security professionals need to think like cybercriminals: allow machines to do the heavy lifting then add in human intervention to execute strategies as successfully as possible.
It is estimated that cybercrime will cost organization a combined amount of upwards of $6 trillion a year. Cybercriminals are getting smarter and to defend networks, predict threats, and protect staff, organizations need increased access to timely intelligence.
Effective information security requires smarter detection techniques which is why many organizations are incorporating AI-driven solutions and products to enable their security teams. However, even with AI assistance the sheer amount of data to assess is encumbering. Signal offers a multi-faceted approach that incorporates filters using boolean logic, AI analysis, and a human hand.
Getting Actionable Insights in Real-Time
In threat intelligence having timely data means everything! Having hyper-relevant intelligence as or even before events are unfolding could mean the difference of several zero’s. By contrast, acting upon old threat insights that maybe have dated can be counter-productive, or even undermine the purpose of the intelligence.
Automation and AI tools can make all the difference when it comes to constantly collecting fresh data. A threat intelligence platform such as Signal which harnesses automation and AI tools massively expands the potential data sources and amount of data that an organisation is able to effectively and efficiently monitor. As well as enabling security teams to sift through all that data and detect anomalous and potentially dangerous activity.
Reacting fast is vital to mitigating threats, but what is even more effective is preempting potential attacks enabling security teams to take preventative measures. For example, using a dark web scan a security team might discover an exploit package for sale targeting a previously unknown vulnerability. Discovering this exploit pack allows the security team to patch the vulnerability before hackers have a chance to take advantage of it.
Automation isn’t Everything
Machines can save you time and in that way they save you money. The combination of AI and Automation when scanning the surface, deep and dark web allows your security team to have more eyes on more data sources. This is vitally important especially today when cyber skills are scarce and data growth so overwhelming. This combination helps prevent analysts from being utterly swamped by endless admin work and allows them to deliver true value to their role.
That being said. Machines can only do so much by themselves (at least for the foreseeable future. People remain fundamentally better at understanding insights from potentially vague context and who are able to deliver an effective response.
Acting fast as we have already mentioned is incredibly important. But just throwing machine learning at the threat intelligence problem isn’t nearly enough. The perfect blend combines rapid and large-scale initial gathering and analysis by machines that then hand-off to their human team-mates to apply strategic intellect while the data is still fresh.
Security professionals have to think how cybercriminals think: machines (e.g. botnets) to do the heavy lifting and a sprinkling of human intervention to execute as successfully as possible.
Injecting Human Intelligence into Automated Threat intelligence
The key to superior threat intelligence accuracy and timing is to leverage automation whilst simultaneously injecting human expertise. You don’t want to be wasting your human resources by making skilled data security analysts wade through piles of admin. Nor do you want those analysts to miss potential anomalous data because your automated system disregarded a seemingly meaningless information package which later turned out to be a viable threat.
Signal allows you to create filtered searches using Boolean logic scanning your chosen data sources and understanding potential location information. These searches can additionally be run through our emotional analysis tool Spotlight.
There is one more problem though. Getting the balance of human and automation right is essential if you want to derive an effective threat intelligence system at a competitive cost.
To solve this problem we have launched our Sapphire program. Sapphire is an optional bolt-on which enables Signal customers to leverage our skilled in-house data analysts to further refine their results allowing their in-house security personnel to spend time on delivering real value.
Final Words
As can be seen from the description above, Signal is not an “AI application” in the commonly understood way. Instead, it’s a system where we use AI techniques and automation in multiple places to create a tool which in the right hands creates an extremely capable intelligence solution.
Even though machines and software will continue to evolve with dazzling speed, the complexity of threat analysis means there will be plenty of challenging opportunities for human analysts for a very, very long time.
Threat Intelligence for Communications and Technology Companies
Remaining aware of the litany of evolving threats that could be and are currently being perpetrated against communications and technology companies is a priority if they want to have any hope of defending themselves against cyber or physical threats.
Communication and technology companies form an integral part of the daily activities of many individuals, companies, and governments. This sector forms a foundation of critical infrastructure which is in part what makes it such an appealing target for cybercriminals.
A successful cyberattack on a company in this sector could see vital services for hundreds of thousands if not millions disrupted. A severed internet connection could see businesses crippled and potentially shut down entire governments.
Remaining aware of the litany of evolving threats that could be and are currently being perpetrated against communications and technology companies is a priority if they want to have any hope of defending themselves against cyber or physical threats.
Telecom operators are adept at protecting their networks, additionally, with the telecom infrastructure being the primary transport for most attacks it’s also true that cybercriminals also have to rely on this infrastructure. This limits the adversaries who directly attack telecom infrastructure largely to anti-establishment hackers.
However, today, telecom organisations are recasting themselves as technology companies - which is why this article encompasses both. For instance, they are creating mobile applications for use of VoIP calls and storing data on cloud services. The lines between technology and communications companies become even more blurred with large tech companies owning parts of the infrastructure as well as those tech companies which have crossed over into the realms of communications. Apple, Facebook, and Google being the most obvious examples.
This cross-over between communications and technology creates new risk frontiers for both communication and technology companies.
“One mounting technology concern is Internet route hijacking, also known as IP hijacking, an exploit in which adversaries corrupt Internet routing tables to ‘hijack’ packets of data. Possible solutions include the implementation of secure Border Gateway Protocol (BGP), a technology that can be used globally. However, secure BGP standards haven’t been consistently adopted, and that’s not likely to happen without government incentives.”
In addition to the growing number of cyber threats, it’s also necessary to consider threats against executives as well as supply chain vulnerabilities which might be exploited. The fact that many of large organisations operate internationally, where materials and equipment manufactured in various different parts of the world is the final part of an ever-evolving ecosystem of threats.
Threats Facing Technology and Communications Companies
Today’s cybercriminals are evolving and adapting fast, discovering and creating new vulnerabilities to exploit constantly. Addressing these threats requires telecommunications and technology companies to have access to up-to-the-minute knowledge and information about threats and vulnerabilities for a vast array of potential attack vectors.
We can divide the main threats facing the communication and technologies industries into two interrelated categories:
Threats targeting companies directly.
These include DDoS attacks, targeted attacks (APT campaigns), network device vulnerabilities and human-related threats like insider access, social engineering and the risk of allowing third parties to access information.
Threats targeting subscribers of services.
Particularly the customers of cellular service providers (CSPs) and Internet service providers (ISPs). These include malware for mobile devices, subscriber data harvesting, end-user device vulnerabilities, and more.
Mobility and the Cloud
Another key issue for these industries is the proliferation of smartphones and internet-capable devices. Despite this being a pressing concern it has been found that technology and communications companies have done little to deploy security measurements with only around 45% of organisations having a mobile device security strategy in place.
As the use of mobile devices increases so does the use of cloud computing services. The cloud has been around in its modern context since at least 2006 however, it is becoming increasingly used by modern organisations with some today 50% of operators currently using some sort of cloud service.
The use of the cloud opens up new business growth avenues and increasingly optimises workflows allowing individuals to work and manage their data from anywhere on any device. However, it simultaneously creates new attack vectors which are compounded by the use of mobile devices.
Whilst organisations share increasingly more data with third parties, vendors, partners, and customers it has been found that a striking lack of security practices exists for IoT and cloud-enabled devices.
67% had an IoT security strategy.
34% had policies for secure collection, retention and destruction of new data.
36% had implemented uniform cybersecurity policies across all IoT devices and systems.
How Communications and Technology Companies are Improving Cybersecurity
Security is everybody’s business. Any member of staff might be exploited as a weakness. In a 2018 survey it was determined that 30% of security incidents were attributed to an employee compared to 23% attributed to an external hacker and 19% attributed to third party vendors. Employees could become threats in a variety of ways, accidentally or maliciously.
For example, they could be personally hacked and extorted for access to protected data. Or they could be a victim of a phishing attack unwittingly installing malware on company devices allowing hacklers to steal packages of data. Or, it could be a location or particular executive that is physically targeted for an attack. The variety of dynamic threats means that it’s not just security teams that need be involved in and informed about threats.
One trend that is true across industries including telecom and technology companies is an increased budget for cybersecurity and threat intelligence.
“It’s predicted that global spending on cybersecurity products and services will exceed $1 trillion cumulatively over the five-year period from 2017 to 2021.”
Another measure is an increasing focus on intelligence. Threat intelligence using tools like Signal allows organisations to efficiently obtain hyper-relevant data in real-time.
How is Signal being used today to protect organisations?
Company data is discovered for sale on the dark web.
Threats to an office location are found in online discussion forums.
Signal discovers an employee sharing sensitive company information online.
Final Words
Today, information security is an advanced discipline that requires the correct technology and processes paired with a skillset based on counterintelligence techniques and supported by top executives. As technology evolves new threats will inevitably appear along with a raft of new challenges.
For companies to mitigate the risks presented by an evolving threat landscape core practices such as employee security training need to be reassessed and continuously updated based on the newest information. The convergence of mobile technology, cloud services and social networking have multiplied risks - and many operators have yet to address many of these increased vulnerabilities.
These factors call for a new approach to security, one that’s driven by the knowledge of threats, assets, and adversaries. One in which security incidents are seen as a critical business risk that may not always be preventable, but can be managed to acceptable levels.
4 Aspects of Effective Executive Travel Risk Management
Businesses have begun realising the importance of reducing travel risks especially for executives where the potential of risk is increased and the potential cost heightened. Signal risk intelligence software enables users to monitor the surface, deep, and dark web to better protect people and assets.
All organisations want to keep their employees safe, this goes across the supply chain and up to top executives. Whether they’re protecting them from the likes of terrorism, upset customers, natural disasters or road accidents, these risks are heightened when employees and especially executives travel.
Whilst threats to travel security are not limited to highly unlikely events, many serious threats like the sudden eruption of a volcano, or terrorist are, thankfully, things that most travellers never have to worry about. However, if COVID-19 has shown us anything it’s that no matter how unlikely a situation may be, they are still a possibility and could escalate incredibly quickly.
Businesses have over the last years begun realising the importance of reducing travel risks especially for executives where the potential of risk is increased and the potential cost heightened. In a 2017 study by Business Travel News of 229 travel buyers and managers and corporate safety and security managers, it was found that “65% said their companies' attention to traveller safety and travel risk management has increased over the past three years.” Ignoring the risks that travel holds could be an expensive mistake.
4 Essentials to Consider for a Effective Travel Security
Reliable Intelligence
Education
Briefings
Planned Response
Reliable Risk Intelligence
Without an accurate risk assessment and a detailed understanding of the potential local risks, a security team cannot make a properly balanced decision regarding operation security. It is incredibly important then, not just for teams to perform risk assessments before travel but to continually monitor local situations so that should things change the security team can react accordingly and take appropriate actions.
For example, as COVID-19 was evolving into a global pandemic security teams needed reliable information from trustworthy sources to allow them to properly understand the potential risks it posed as well as to navigate through the plethora of misinformation being spread. Teams using Signal OSINT were able to get this information and take preventative actions, putting secondary measures into place should the situation evolve. In this particular example, extreme action was needed. The security teams first suspended all executive travel to badly affected areas and as the situation evolved into a more serious global crisis they evacuated executives and employees who were overseas, before entirely suspending further business travel.
Without the proper information, the best course of action cannot be pursued. Situations change rapidly and timely intelligence will provide detail on current and future anticipated threats.
Staff Education
As part of an effective travel security program staff need to be aware of the potential dangers and have the tools and knowledge to minimise and mitigate personal travel risks. Risk can be dramatically reduced with good basic personal security methodology which is often the most cost-effective and efficient way to improve the safety of employees abroad.
Part of this education must be an ongoing effort to share with the relevant parties this real-time information from data sources gathered through tools such as Signal.
Debrief
With properly trained staff, the individuals travelling should be aware of the environment, threats and risks that they are entering. On top of this, as we mentioned above this information sharing should not stop at the briefing, but as the threats evolve the relevant individual needs to be kept up to date so that they can change their behaviour if necessary.
A Planned Response
The fourth aspect of an effective travel risk management plan is having planning a response to all possible crises. In certain locations, some aspects and threats are more prevalent.
For example, emergency services might be lacking or public transport might be more dangerous. In these cases, proper plans need to be put in place. For the latter, you might arrange a rental car for your executive, or a driver, if the road laws are known to be difficult. These preventative actions remove several potential threats which would be far more costly for the business than the cost of something like a driver.
There must be a pre-identified and rehearsed service in place to ensure an effective and timely response to an emergency.
Three main parts to an effective response include:
1. Prevention – The best security avoids or prevents threats from becoming risks. A good benchmark is to be able to identify the exact location of your employees and be able to effectively communicate with them within 15-20 minutes of an incident occurring.
2. Crisis Management – If a crisis does happen, the first thing you need is an effective communications channel. Through this, you need to be able to quickly implement plans and processes to manage the evolving crises.
3. Evacuation or Hibernation Plans – If a situation escalates beyond a certain point it may be that security teams need to implement and evacuation or hibernation plan. Which will either have the executive returned home, or hibernate in-situ until the situation changes. An example of a necessary evacuation plan being implemented would be in response to the Corona Virus. With only a little warning it became apparent to those organisations who had teams or individuals in Wuhan China that they needed to get them out of their fast. This situation then escalated rapidly to become a global crises.
Challenges
Travel security and executive protection comes with a number of challenges. It doesn’t look good to put a large amount of money into executive protection, however, there needs to be a balance to avoid potential risks. If an executive is attacked, or involved in an accident whilst abroad then shareholder value may drop, potentially for days, and sometimes the pressure in these scenarios can have negative effects long after the incident.
A situation can change rapidly, requiring a different response even as soon as hours later., which is why having real time intel of an event is so crucial. With the right systems in place and the right tools in the security teams toolbox, threats can be identified, monitored, and effective preventative measures and contingency plans put in place. All of this acts to protect both the individuals and the company involved.
The Role of OSINT in Managing Executive Safety During Travel
The modern workforce is more decentralized than ever. As employees travel or work remotely, it is important to know about potential issues that could impact their safety and security. Signal can assist with early warnings of:
natural disasters in or near destinations;
potential travel disruptions;
terror attacks;
security threats;
political or economic indicators.
Signal Open Source Intelligence software allows you to gather real-time data. More importantly Signal allows users to tailor their feeds to get customised data relevant to their particular situation. Which means instead of having to monitor every part of the web manually you can instead get customised filtered alerts.
On top of this, Signal risk intelligence software enables users to monitor the surface, deep, and dark web. Many dark web forums don’t allow strangers to access their sites and require authenticated logins which makes it even harder to gain access on to these sites and monitor potential risks that occur in these places which security teams need to be aware of such as data breaches, threats of physical attacks and terrorism.
Learn more about how Signal can improve your executive protection…
Responding to Global Crises like COVID-19 with Increased Situational Awareness
In the wake of a global incident, corporations need fact-based reliable information from official sources and they need it fast. The smart adoption of technology can help facilitate the means for companies to protect their teams and assets as well as mitigate potential damages to the business.
Corona Virus has for many been a rude awakening. Companies have been left scrabbling in an attempt to put in place contingency plans and deal with the spread of misinformation, all whilst facing tumbling share prices.
COVID-19 is the most recent global incident, it’s not the first and it won’t be the last, however, it has thrown into harsh light the realities and weaknesses that surround many organisations international structure. Our increasing levels of globalization throw local isolationist policies out the window and if a company wishes to maintain economic growth changes in the way that they manage their response to global incidents is needed.
In the wake of a global incident, corporations need fact-based reliable information from official sources and they need it fast. The smart adoption of technology can help facilitate the means for companies to protect their teams and assets as well as mitigate potential damages to the business.
Dealing with Misinformation: Disruption is the new normal.
The rapid spread of news and information online has sparked a recent increase in global headlines highlighting critical outbreaks. International concerns can cause loud and distracting noise when trying to identify specific data.
On top of this, panic has followed in the wake of COVID-19, stocks have plummeted to levels that haven’t been seen since 2008, people are rushing to stores to stock up on necessities. This panic has been spread and amplified by both a lack of preparation for a global crisis of this nature, as well as an amount of misinformation spread rapidly through both social media and even through more trustworthy news sources.
To tackle this, the first thing any organisation needs is accurate, relevant and trustworthy information. You don’t want to be relying on secondary, potentially egregious sources, not only because it will take longer to uncover news forcing, but you also won’t know how reliable that information is. Sad as it may be to admit, many media outlets aim to sell news, and facts aren’t necessarily lucrative, spectacle sells.
Using an open-source intelligence (OSINT) software like Signal you can create a custom real-time stream from official sources such as the World Health Organisation, or the CDC to get reliable information and updates fast. Easily sift through unwanted information to detect only the most valuable in an outbreak.
Better situational awareness for a more efficient response
Increased situational awareness allows companies to proactively respond to crises. It allows them to get accurate information first, and create actionable and effective strategies based on reliable data to efficiently counter emerging threats.
As well as having multiple sources, companies can use OSINT tools to identify trustworthy and “official” statements and sources and tailor their live stream searches around those. This is often where the news breaks first and will give an unbiased account of the facts.
Examples of responses to COVID-19 can be seen from several large companies including Facebook and Amazon. In areas where there are outbreaks, such as Seattle, they have closed down offices and asked employees to work from home. They have also both cancelled conferences which would have drawn thousands of people together with potentially disastrous results - instead they are looking at creating a virtual experience instead. This is just one example, of how companies, armed with accurate information can then use available technology to facilitate preventative measures mitigating the threat of the outbreak.
How OSINT software can help
Improve employee safety
Knowing how to respond and then implementing an effective response without causing further panic or further spreading misinformation allows organisations to effectively protect their staff in and outside of the office.
For example, knowing how COVID-19 is spread as well as understanding the the severity and location of the outbreaks means you can form effective localised preventative measures without causing undue widespread panic or unnecessarily harming your business.
Better executive protection
Executives travel, and travel entails risk especially with an evolving international crisis of this nature. In this scenario, for example, it would be sensible to protect these executives by taking simple precautions such as delaying trips to areas with severe outbreaks such as China or Italy.
In line with current government recommendations all employees should be practicing social distancing and where possible managing meetings with video conferencing technology. Adapting in the face of an emerging threat such as COVID-19 allows companies to reduce the risks that they face and better protect their staff from exposure.
Supply chain management
Those businesses that are built on the foundations of large and complex international supply chains have to question their structure and practices. What is the backup plan? How do you mitigate the threat to a potentially compromised supply chain? And perhaps, more importantly, how do you protect those staff and assets that are involved?
First, you need actionable and accurate information in real time allowing you to fully understand potential risks and issues and only then can you form an effective plan of action.
Summary : The Importance of Accurate Real Time Data
Coronavirus is the only the latest example of a disruptive global crisis and it won’t be the last.
Due to the rise of unofficial media sources which can easily disseminate news through the internet, especially social media platforms, there is a lot of potentially unreliable information being consumed. Fact-checking can be immensely time-consuming and many people don’t bother, which is how false information propagates. As an organisation though this misinformation can be as harmful or even more harmful than the reality. Getting ahead of and tackling false news becomes an important task.
In terms of dealing with a global crisis such as COVID-19, think about spreading fact-checked sources through internal communications to allay fears spread through potentially incorrect or misleading media. This will also show employees that you are on top of the situation encouraging trust in the organisation and your official response.
To truly and effectively mitigate the threat of global incidents, how companies utilise technology to adapt to the scenario will make a huge difference. Ask yourself: Does your business offer flexible working practices? How can your business support workers if they need to self-isolate? Do you need your executives to attend events in physical locations or can business be done virtually? And as a final consideration - a side effect of these changes - how might these adaptations become more normalised to improve employee efficiency as well as supporting a healthier work life balance?
Resources
Why a Dark Web Scan is Essential for your Business
With the right tools, like Signal threat intelligence software, monitoring and filtering through information on the dark web is entirely possible without ever needing to download a Tor browser, allowing users to effectively protect their staff, customers and assets.
The dark web is a layer of the internet that is only accessible through an encrypted browsing software such as a Tor browser. This software makes the user anonymous. It is this anonymity which is so beneficial to criminals who are able to trade illegal items and services.
Cybercriminals are known to buy and sell stolen data, for example, which can be used to commit identity theft and fraud. Many of the overtly criminal websites require membership logins that you can only gain if you are active as an online criminal making it challenging for companies and security forces to access and monitor these websites.
However, with the right tools, like Signal threat intelligence software, monitoring and filtering through these websites is entirely possible without ever needing to download a Tor browser yourself.
What is dark web scanning?
A dark web scan monitors open-source information available on the dark web, using both human and artificial intelligence to scan things like criminal chat rooms, blogs, forums, private networks and other sites. In doing this it helps organizations detect potential security threats.
Examples of activities that have been identified from dark web content using Signal Threat Intelligence software include;
Online markets selling stolen and fake goods;
Hackers selling non-sensitive data for use in credential stuffing attempts;
Impersonation of individuals or organizations;
Details in regard to hacking or incitement to hack;
Reputational risk via fake news or impersonation;
Illegal activities such as drugs and drug paraphernalia;
Information regarding a previously undetected sensitive data breach.
What happens during dark web monitoring?
There are some 55,000 dark websites, however, many of these are inactive and even fewer of them are actually used for overtly criminal activity. During dark web scanning our security software monitors and detects any data that is relevant to the particular search queries that have been set up. This allows you to create a customised highly relevant stream of data and information around key points of interest for your company.
The information can also be run through a sentiment filter to create an even further refined stream of data, we explore this in further detail below.
Why is dark web monitoring with Signal Corp important for businesses?
1. Detecting data breaches
Our software has been used to identify stolen credentials and other personal information that is circulating on dark web networks and other channels.
To identify relevant data you are able to set up specific search queries within the software. These constantly monitor the open, dark and deep web and then filter these searches using our AI technology to determine what is and isn’t relevant. We then add a human touch to the remaining data to further filter using human intelligence to identify what is highly relevant.
The scan infiltrates private sites - many of which require membership within the cybercriminal community to enter.
When it comes to detecting data beaches it can quickly identify chat around data that is circulating online which has been gained by illegal hacking attempts. If data is detected from a particular company, whilst there is no way to retrieve that data organisations can take precautionary measures to mitigate the damage and threat of the data breach as well as determining how the data was gained and ensuring that breach is secured against further data beach attempts.
2. Detecting Physical Threats against People and Assets
The big draw for criminals to the dark web is that all users need to use an encrypted browser to access the dark web which entirely anonymises their presence. This means, very simply, that criminals can and do talk about their activity, either to brag or as part of their preparations.
Using software like Signal you can constantly monitor the dark web and when a criminal talks about or potentially threatens one of your staff or assets you can know instantly. Whilst they are anonymised and you won’t know who is planning something, you will know that there is a very real potential threat that you can now guard against.
3. Predicting potential terrorist actions
In the same vein as detecting potential physical threats against a company online, the dark web is also a place where terrorists go to communicate and organise. By monitoring the dark web then you can pick up on their conversation and use the data gathered to potentially predict and deter terrorist attacks aimed at the company.
How do you determine when chat becomes a serious threat?
One of the potential issues some of our customers face is the sheer amount of noise which might surround their brand. Invariably not all of this noise is good. Which is why we have a sentiment analysis tool to help filter out what chat, what noise online we need to pay attention to.
On top of this, this can then closely monitor individuals who have been detected to hold negative sentiments towards a customer and it can determine if that was a once-off comment, or if this negative sentiment might actually evolve into a more palpable threat.
Seeing in the Dark - Exposing the Dark Web
In 2017 we launched our dark web monitoring functionality. From there we have evolved it into an invaluable part of our security intelligence offering which is used by corporate security teams across the globe.
There is plenty of online information regarding the dark web – mostly accurate, although it can be daunting to understand the various nuances. There are numerous benefits that come with monitoring of the dark web.
When it comes to dark web monitoring, Signal risk intelligence software offers a comprehensive service which enables security professionals to gain increased situational awareness using targeted, highly relevant data gathered from dark web sources.
Why did we add Dark Web monitoring to Signal threat intelligence software?
The Dark Web is the place to lurk out of sight, with complete anonymity, which makes it a logical centre for criminals to gather, discuss illegal activity, and sell illegal goods and services. Because of this, those bodies and security teams which are able to effectively monitor the blogs, forums, and chat rooms of the dark web have an invaluable source of information on nefarious or illegal activities - and are often among the very first to know about important and relevant information that may impact their company or organisation.
Advanced warning for things like data breaches, reputational risks and physical threats to assets allow companies to effectively form strategies to deal with and mitigate the threats to their organisations.
These conversations and activities are highly relevant to many Signal subscribers, hence the addition of the Dark Web as a data source for Signal Gold subscribers in 2017.
Read our articles:
Examples of activities that have been identified from dark web content include:
Online markets selling stolen and fake goods
Impersonation of individuals or organizations
Details in regard to hacking or incitement to hack
Reputational risk via fake news or impersonation
Illegal activities such as drugs and drug paraphernalia
One of the benefits that Signal provides is the ability to review the dark web post content without needing to utilize a Tor browser – simply review the content from within your Signal browser session.
Dark web monitoring is available for Signal subscribers with a gold or better subscription– if you are interested in more information in regard Signal or the dark web content, then contact us info@signalpublicsafety.com