The Threat of Doxing to Organizational Security
Organizational doxing is on the rise and can be immensely damaging, exposing company secrets and customer data, or more directly exposing executives to new levels of threats.
What is Doxing?
The term itself originates from the phrase “dropping docs” and was later shortened to “docs” and then “dox”. As the original term suggests, doxing is when someone collects and then shares information about another person or organization.
There are numerous reasons someone might dox someone else or be the victim of doxing. It could be for revenge or a personal grudge, a disgruntled ex-employee might target their previous employer, for example. In 2014, Sony was the victim of a doxing attack backed by, experts believe, the North Korean government after they released a film which made fun of their leader. Other motivations include harassment and cyber-bullying, vigilante justice (for example, exposing neo-Nazi’s), and doxing for financial gain.
Organizational doxing is on the rise and can be immensely damaging, exposing company secrets and customer data, or more directly exposing executives to new levels of threats.
Doxing Strategies and Goals
Traditionally doxing started with an online argument escalating to one person digging out information on their adversary and sharing it online. More recently though, doxing has become more of a cultural tool with hackers taking down people or groups with opposing ideologies. When it comes to organizations, threat actors have been known to both target an organizations reputation and to use information gained through a doxing attack to leverage financial reward.
For example, in one scenario an employee at a bank was blackmailed after a doxing attack into using his position in the bank to steal over $100,000 from customers for his blackmailers.
The fallout is generally reputational with the victim suffering from online abuse such as death threats to them and their family in lieu of the new information shared. However, on occasion, the fallout can be significantly worse. There have been examples of mobs dishing out physical vigilante justice after a person's information, such as an address, was shared online.
There are numerous ways you can be identified online. By following ‘breadcrumbs’ of information a dedicated doxxer can assemble an accurate picture of a person - even if they were using an alias. The kind of details they might look for include, full name, current address, email address, phone number etc. Additionally, some doxxers might buy information from data brokers.
IP/ ISP Dox
There are various methods that can be used to locate your IP address, which is linked to your location. With just your IP address a doxxer could then use social engineering tactics against your Internet Service Provider (ISP) to discover the information they have on file such as:
Your full name
Email address
Phone number
ISP account number
Date of birth
Exact physical address
Social security number
This requires the doxxer to go through a dedicated process, which may not even work, however, it’s just one strategy they can employ, and even if they are unable to gather further information through a gullible ISP worker they still have the first parts of the puzzle - your IP address and a rough location.
Doxing with Social Media
If your social media accounts are public then anyone can view them. Often things a threat actor can find out include your location, place of work, your friends, your photos, some of your likes and dislikes, places you’ve been, names of family members, names of pets, names of schools you attended, and more.
With this kind of information, they can then find out even more about you, or even discover the answer to your security questions helping them break into other accounts such as your online banking.
As such it’s recommended to keep your social media profiles private, and if you use multiple online forums to use a different name and password for each to help prevent doxxers from compiling information from across multiple online forums and social media sites.
Data Gathered through Brokers
Data brokers on the internet collect information from publicly available sources and then sell the data for profit. Generally speaking, they sell this data to advertisers - if you’ve ever found yourself randomly receiving emails from companies you’ve never heard of before, this is why. However, for a doxxer it could be an easy way to start building a detailed profile of their target.
How Might Doxing be Used Against Your Organization?
For organizations to be successful with their media strategies they necessarily need to share relevant information and regularly engage with their customers through social media channels. This provides a substantial opportunity for doxxers.
By combining publicly-available data with basic attack techniques, such as phishing campaigns or credential stuffing, malicious actors can uncover large quantities of supposedly secure data. For consumers, exposed information could lead to identity theft or public shame. Meanwhile, companies face the prospect of large-scale reputation damage or lost revenue if proprietary project briefs or intellectual properties are leaked to the public.
Additionally, doxing can be used as an incentive to expedite the resolution of ransomware attacks. This is where the cyber attacker threatens to release documents or information to the public should their target not pay the ransomware fee promptly. This adds to already serious financial implications.
How Can you Prevent Doxing?
Unfortunately, it's nearly impossible to completely remove personally-identifying information from the internet, especially parts which are part of public records. Still, there are some tips to reduce your attack surface.
Keep your profiles private
People and organizations do have a lot of say as to what gets published on the internet. Make sure to practice general data privacy best practices.
Avoid posting identifying information
Keep all social media settings at the most private level, and don't accept friend requests from people you don't know
Change the settings on Office and your phone's photo app so personal info isn't embedded in those files
Use a "burner" email address for signing up for accounts when possible.
Set the ‘whois’ records on any domains you own to private
Ask Google to remove personally available information about you, and request the same from data broker sites
Implement Safe Browsing Measures
These steps are good internet hygiene in any case, but can also prevent a breach that can lead to your info being exposed to a potential doxxer:
Use a VPN, especially when using insecure public Wi-Fi networks
Switch to a secure email system with built-in encryption
Vary your usernames and passwords
Self-Doxing
Humans remain the weakest link in the security chain. In most cases, malice isn’t the problem or the intent when someone lets a threat actor in. Instead, employees overshare personal data on corporate platforms by accident or use insecure third-party applications. In both cases, however, following the breach and identifying the potential compromises is difficult when IT teams start from the side of defenders.
By flipping the script and looking at your organization from the view of potential doxxer it becomes easier for IT and security teams to spot key areas of weakness. They can then develop strategies and staff training programs to protect against them.
Final Words
Doxing represents a growing threat to organizations and individuals. However, by self-doxing with security intelligence gathering strategies, security teams can create accurate attack surface maps. With this intelligence, they can then enhance threat modelling and deliver actionable insights to staff to reduce overall risks.
Using OSINT software like Signal you can learn about potential threats as or before they occur, learn about potential exploits targeting your organization, and self-dox to help identify weaknesses and shore-up defences.
How Monitoring Current Events Like the 2020 US Election Can Increase Organizational Security
Tensions around the US election are high for both ends of the political spectrum. There has been an increase in polarization and militarization and many Signal customers have expressed concern.
There are numerous threats that could evolve to seriously impact an organization, from natural disasters, to acts of terror, to targeted attacks on executives. Currently though, tensions around the US election are high on both ends of the political spectrum. There has been an increase in polarization of political views and even militarization of the public in recent months, and many Signal customers have expressed concern.
For many American’s this is seen as the most important election of their lives so far. Fears of voter fraud and voter suppression are rife, which is reflected by an unprecedented number of early votes being cast with more than 90 million votes already cast a week before the election, more than two-thirds of all the votes cast in 2016.
This, paired with a deadly pandemic and a summer of protests, many of which became violent, and one can see the potential for civil unrest around a contentious presidency. To mitigate this risk organizations need relevant intelligence as events unfold to ensure they take the necessary precautions to protect their employees and assets.
As such, we have created advanced tools to enable Organizations to be alerted as early as possible to issues and current events, such as the Election, where the possible fallout could have an impact on their employees and assets.
Monitoring Election Threats in Real-Time Using Signal OSINT
Using Signal security teams can learn of events as they are happening or even before they happen, allowing effective response plans to be enacted, effectively neutralising potential threats.
To do this users can create custom searches using Boolean Logic to filter intel from key web sources such as social media, the open web, and the dark web. Intel from these sources often acts as an early indicator alerting Signal customer to potential issues in real-time. The data can also be reviewed by our emotional analysis solution for increased data analysis efficiency.
Signal has real-time SMS and email alerting for high-risk threats so that companies can maximise available response time. Once alerted to potential risks the security team can form a final judgement on the threat level and decide whether action needs to be taken.
Final Words on Threat Monitoring with Signal
Threat monitoring isn’t just for events such as a contentious election. COVID-19, earthquakes, storms and other extreme weather events, and even threats of violence against specific executives, can all affect an organization. Signal OSINT software enables security teams to scan a vast number of surface, deep, and dark web channels and sources to gain real-time data on a broad array of emerging threats.
Anonymous social media forums like 4chan or dark web forums are often where threat actors go to communicate and organize. And social media is often where you can learn of current events as they unfold. So whether it’s customer data for sale online, or an active shooter situation in-store, security teams armed with OSINT can quickly assess and respond appropriately to mitigate risks and damages.
Only when an organisation has a complete picture that incorporates the variety of potential risks and has invested in specific responses and contingency plans can it adapt as needed to mitigate the impact of extreme events.
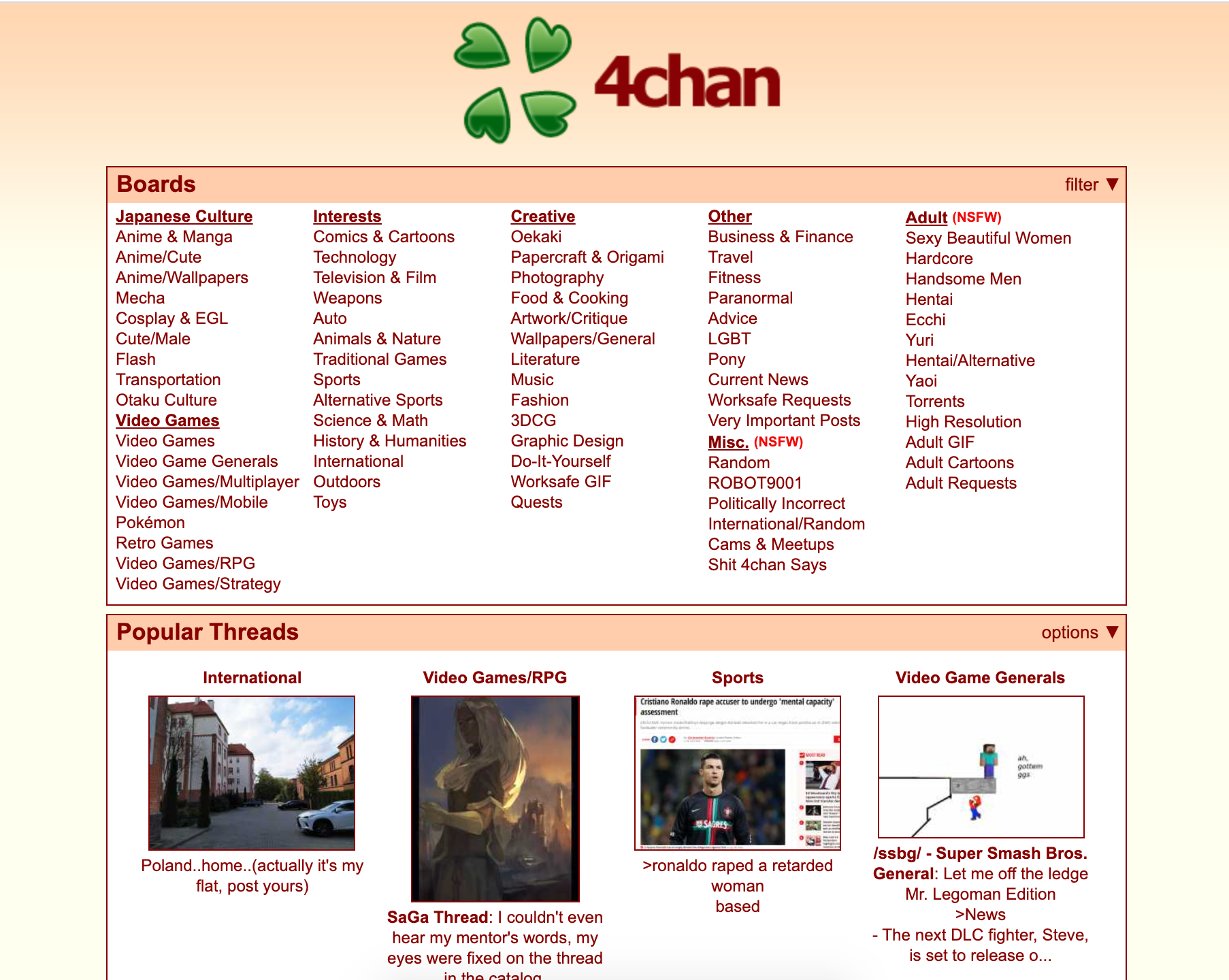
How can 4chan be Used as a Data Source for Security Intelligence?
4chan is just one of the data sources you can monitor using Signal. You can find conversations by alt-right groups, threats of violence against a person, organization or group, and more, which makes it a valuable data source for security professionals.
What is 4chan?
4chan is one of the largest English language based image boards on the open web. They have over 900k new posts per day and some 27 million active monthly users.
What makes it a unique social platform is that users can choose to remain anonymous. They don’t even need to create an account to access and engage with content on the platform. As an added security measures, posts time-out after a period so they can’t, unless found and archived by an independent data gathering source, be checked and referenced by security teams, users, or law enforcement at later date.
There is a wide range of topics hosted on the platform, from Japanese culture, to politics, to adult content. Because of the anonymity allowed, as well as a very limited moderation by the site owners, 4chan has a large amount of illicit content and activity. This activity includes cyberbullying, child pornography, harassment, violent threats, racism and extremist ideologies.
Despite this, it’s important to note that there is nothing inherently bad about the platform, just as there is nothing inherently bad about the dark web, and many of the users use it for legitimate purposes such as for its original intent which is the exploration and discussion of the Japanese film and television animation style, anime. In fact, like Reddit, many influential memes have originated from the platform such as ‘lolcats’ and ‘chocolate rain’. As such it has historically been an important driving force behind the development of internet culture.
Bottom line: 4chan is a forum, the original purpose was for the discussion of anime and Japanese culture. It’s a forum where users don’t need to have an account or sign up with a name, there is little moderation, and posts are deleted from the server after a period, as such there are few consequences. With this format, people can and do say just about anything on the platform.
How can 4chan benefit your organization as a data source?
The anonymity offered by the channel means users feel comfortable talking openly and they do so around a wide range of subject matters and people. For example, under the political forum /pol/ you can find examples of alt-right groups, threats of violence against a person, organization or group, and racist behaviour.
The range of topics discussed and the freedom with which individuals and groups openly discuss them can give security teams and law enforcement an idea of emerging trends as well as be one of the first places that death threats or threats of violence against individuals and organizations can be found. In the past, terrorist manifestos have also been posted on the channel. These discussions can indicate when an event is going to evolve into a tangible threat and give security teams a heads up to prepare and mitigate the potential threat.
Additionally, there are groups and individuals on the channel, such as the members of Anonymous who have turned their online attention, for right or wrong, to intelligence gathering on people and organizations. Often, 4chan is one of the first places they share their findings. For example, they might uncover and share personal details about a CEO such as their address, medical records and details of their family.
Why use Signal for monitoring 4chan?
One of the key problems with any form of online intelligence reconnaissance is the quantities of data you need to assess to get even the smallest tidbits of potentially useful information. 4chan has this problem in spades with over 3.5 billion posts. And these posts are transient, with the more R rated the post being the shorter it’s existence. This means relevant security intelligence on the 4chan platform might only be public for a couple of days. To gain real insights into the channel you need to be constantly and efficiently monitoring with real-time alerts.
4chan is just one of the data sources you can monitor using Signal though. You can simultaneously monitor the open, deep, and dark web including forums like Reddit and chatrooms like Telegram. Our system allows you to create tailored keyword-driven searches with boolean logic which is assisted by our machine learning and language processing AI to efficiently gain intel on hyper-relevant, new and emerging threats.
6 Ways Signal OSINT is Improving Protection for Executives and VIPs
Security teams need to be able to spot threats to executives and implement an effective response in a timely fashion. In this article, we take a look at 6 key areas that Signal OSINT is used by customers today to advance protection measures for high profile executives.
High profile executives and VIPs are more likely to receive threats of violence, be at the centre of negative online noise, and to be the target for both cyber and physical attacks. This, when paired with their busy schedules (which often involve travel), makes staying ahead of potential threats a particular challenge for their security teams.
Attackers have a variety of reasons and goals for targeting executives and VIPs. It could be anything ranging from a reaction to company layoffs, to kidnapping for ransom. Whatever the reason though, security teams need to be able to spot the threats, understand the motives, and implement an effective response in a timely fashion.
In this article, we take a look at 6 key ways Signal OSINT is used today by customers to advance protection measures for high profile executives.
How Can Signal OSINT Improve your Executive Security?
Discover private information published online
There are several reasons that an individual might publish private information online. Often, it is in anger or as some form of revenge. The kind of information that has been found published online includes: names, email addresses and logins, physical address, details about an executives families, passport details, medical information, credit card and bank details, and SSN’s.
Having such information leaks opens up an executive to a wide range of potential threats. As a security professional, it is vital to know if and when there is a data breach so that the threat can be neutralized. The longer data is available online the more risk there is. For example, if card details are discovered online the bank can be contacted and the card cancelled.
Read: Detecting and Mitigating the Risks of Data Breaches
Identify direct threats
Sometimes threat actors are more direct in the way they threaten executives. This could, for example, be a direct threat of violence through an email, instant messaging service or public forum like social media. While the majority of such threats come from so-called “keyboard warriors” there are some which will require further attention and action.
For example, discussions might be uncovered on the dark web forum with details of a planned attack on an executive. With the prior knowledge of the attack action can be taken to reduce the associated risks.
One way to differentiate between someone that is simply venting their anger on a public forum and someone who genuinely might take action is to look for repetition of negative sentiment.
Emotional analysis
Emotional analysis gives data extra context which allows it to be better understood enabling a more effective and accurate response to the potential risks.
It also allows you to differentiate between when a negative comment is simply that, a negative comment, or when it needs more serious attention, for example, it’s evolving into a physical threat.
Read: When Does Negative Sentiment Become a Threat?
Misinformation is spreading about an executive
The spread of disinformation is problematic on a number of levels. For example, throughout COVID-19 misinformation has been spread regarding the virus, it’s root causes and best prevention practices. This has harmed efforts to curtail and control it. Another recent example is the role of misinformation in the 2016 US election.
There are numerous reasons that individuals and organizations spread misinformation, it could be part of a phishing campaign or an international political assault, for example. Whatever the reason the results are almost always harmful. When an individual spreads misinformation around a CEO or other executive there are real ramifications for brand and reputation which need to be managed.
To combat misinformation organizations need to be equipped with the right tools and understand both what they’re looking for, and the reasons for spreading misinformation.
Disruptive events are planned which could prove a threat to executives.
Events such as protests planned at or near an office or manufacturing location could present logistical problems and delays as well as potentially devolve into riots which would represent a physical threat. Having intelligence on the events and any salient information regarding individuals or groups looking to create trouble will allow you to take appropriate precautionary measures and prevent a threat from escalating.
Travel risks
All travel comes with some inherent risk. However, it is more pronounced for executives who are at increased risk due to the regularity of their travel and high profile.
Additionally, events like extreme weather or terrorist action may make a destination unsafe. As such, having an OSINT solution such as Signal offering an early warning of any particular dangers will enable you to plan alternative routes and otherwise avoid high risk scenarios.
Read: 4 Aspects of Effective Executive Travel Risk Management
Early warnings with real-time data
Using Signal you can create customized alerts filtered via specific keywords, phrases or even locations. We also have a built-in translation tool so that data can be searched across languages and automatically translated into your default language.
Additionally, you can run alerts through our emotional analysis tool to determine how much of a threat any particular alert is. Finally, get our optional Sapphire bolt-on and utilise our skilled data analysts to further refine your results.
This approach allows your leave your intelligence gathering on autopilot and not only effectively reduce costs but vastly increase the scope of your monitoring ability and the overall amount of hyper-relevant intelligence at your fingertips. All of this allows you to gather actionable intel in realtime.
What is Ransomware and Why Should you Care?
Ransomware attacks are becoming more complex and brazen with big companies like Garmin in their crosshairs. What do security professionals need to know about ransomware attacks, and what measures and precautions can they take to mitigate the potential damages?
Ransomware is big money and is a rapidly growing cyberattack strategy. The market has expanded massively since the advent of secure and untraceable payment methods such as Bitcoin. Emsisoft estimates that ransomware costs for US organizations in 2019 was in excess of $7.5 billion. Compare this to four years prior when in 2015 ransomware damages totalled around $300 million.
Some markets are particularly prone to ransomware attacks such as medical organizations and public services. And there have been several high profile cases involving these industries over the last few years. Attackers know that with lives literally on the line organizations in these fields are likely to simply pay the ransom to make the problem go away. Most recently Garmin technology company has been held to ransom with attackers using the WastedLocker ransomware seeking a ransom of USD$10 million.
In this article, we explore in detail what ransomware is, how cybercriminals utilize and what strategies organizations can employ to ensure they are protected from ransomware attacks.
What is Ransomware?
Ransomware is a form of malware. It can take various forms but generally it functions in one of two ways:
Crypto ransomware. This malware encrypts the files on a computer so that the user cannot access them.
Locker ransomware. This malware locks the victim out of their device or out of particular files, preventing them from using it.
One thing all ransomware attacks have in common is that the target won’t be able to regain access to their files unless they pay the attackers a hefty ransom to unlock the files.
Ransomware has grown in popularity over the last few years in the wake of cryptocurrencies which makes it safe to receive their ransom payments. The cost of a ransomware attack can range from a few hundred to thousands of dollars depending on who the target is and how valuable the attackers believe the files they have locked out of reach are.
Probably the most common delivery system for ransomware is phishing scams. For examples, a virus masquerading as an email attachment can, once downloaded and opened, easily take over a victims computer. Another strategy is through social engineering which is growing in popularity with cybercriminals because of the better strike rate. A recent example of a successful social engineering attack was perpetrated against Twitter employees. Attackers were able to get aways with an estimated 12.85BTC, nearly US$120,000.
The encryption strategy for malware is the more common of the attacks. The result of this attack is that the victim will not be able to decrypt their files without a mathematical key known only to the attacker. The user will be presented with a message when they attempt to open their files saying that their documents are now inaccessible and will only be decrypted if the victim sends an untraceable cryptocurrency payment to the attacker’s wallet.
To encourage prompt payment attackers might masquerade as law enforcement and demand the payment as a fine. If the victim does have illegal or illicit files or programs on their device, such as pornography or pirated software or movies, then they may be more likely to pay without asking questions and without reporting the attack.
12 Ransomware Examples from the Last Decade
Ransomware has been around for decades. However, it was only after the advent of cryptocurrencies that it began being a favoured strategy for cybercriminals. Cryptocurrencies allow for them to collect untraceable completely anonymous payments. Some of the worst offenders have been:
CryptoLocker is an older malware threat, and while it isn’t in broad circulation anymore during it’s peak it infected some half a million machines. Cryptolocker is a Trojan horse that infects a device computer and then searches the computer as well as additional connected media including; external hardrives, cloud storage, and USB sticks, for files to encrypt.
TeslaCrypt is a variation or copycat of CryptoLocker. TeslaCrypt started by using social engineering to infiltrate devices and later used phishing emails as well. It heavily targeted gaming files and saw numerous upgrade improvements during its reign of terror.
SimpleLocker was another CyrptoLocker styled malware. However, it’s key difference was that it focused it’s targeting on Android devices.
WannaCry is a ransomware worm. What this means is that it spreads autonomously from computer to computer using EternalBlue, an exploit developed by the NSA and then stolen by hackers.
NotPetya also used the EternalBlue exploit. It is thought to be part of a Russion-directed cyberattack against the Ukraine. However, it expanded autonomously to infect a broad range of organizations.
Leakerlocker was first discovered in 2017 and targeted Android devices. Rather than encrypt files, it threatens to share your private data and browsing history unless you pay the ransom.
WYSIWYE, stands for “What You See Is What You Encrypt”. Discovered in 2017, this ransomware scans the web for open Remote Desktop Protocol (RDP) servers. It then allows for a customized attack with an interface through which it can be configured according to the attacker’s preferences.
SamSam has been around since 2015 and has affected devices in a number of waves of attacks. It utilizes vulnerabilities in remote desktop protocols (RDP), Java-based web servers, file transfer protocol (FTP) servers or brute force against weak passwords It would then spread to numerous devices. It primarily targeted public services and healthcare effectively bringing entire organizations to halt.
Ryuk first appeared in 2018. It is specifically used to target enterprise environments. It is often used in combination with other malware like TrickBot for distribution.
Maze was first discover in 2019. The MAZE ransomware has been used in attacks that combine targeted ransomware use, public exposure of victim data, and an affiliate model. The ransomware was initially distributed via spam emails and exploit kits before later shifting to being deployed post-compromise.
GandCrab currently holds a large portion of the ransomware market and may well be the most lucrative ransomware ever. Its developers, which sold the program to cybercriminals, claim more than $2 billion in victim payouts as of July 2019.
Thanos is a Ransomware-as-a-Service (RaaS) operation which allows affiliates to customize their own ransomware through a builder offered by the developer. It was first discovered by security professionals being talked about on a Russian darknet forum. It is the first to use the RIPlace technique, which can bypass many anti-ransomware methods.
Dealing with Ransomware
Prevention is always the best policy when it comes to dealing with cyber attacks. Using tools such as Signal you can stay up to date with the most common strategies and one step ahead of cybercriminals. However, if you become the victim of a ransomware attack, it is advisable not to pay the ransom. If you do so there is now guarantee that the cybercriminal will return your data, they are thieves after all. Additionally, it fuels the profitability of the ransomware business making future attacks more likely. So what can you do?
Decryption
For many ransomwares, especially the older ones there are decryption tools which have been developed. The first step then is to contact your internet security vendor and determine if decryption is possible. If this initial strategy fails you can visit nomoreransom.org. The No More Ransom site is an industry-wide initiative designed to help all victims of ransomware.
Recovery
It’s good practice to back-up your data regularly on both external hard drives as well as on cloud storage. If you have done this it becomes possible to simply recover the data which is currently being held hostage. There are of course some scenarios where this won’t be possible, for example, if the malicious actor is threatening to share private information rather than having simply encrypted your device.
Preventing Ransomware Attacks
Good security practices will help prevent you from falling victim to ransomware. These defensive steps will additionally help protect you against other generic cyber attacks.
Four basic steps that every organization should take to mitigate the threat of cyber attacks are:
Keep all operating systems up to date and patched. Doing this will ensure that there are few potential vulnerabilities that malicious actors can exploit.
Do not allow a software admin privileges unless you are confident in its safety and know exactly what it is and what it does.
Ensure you have an active and up to date anti-virus software installed on all devices. This will allow you to detect and block malicious programs like ransomware as they arrive.
And, as we said in the section above, back up all your files regularly. This last point won’t help protect against ransomware or other malware but can help mitigate the damages that your organization might suffer.
The Role of OSINT in Defending Against Ransomware
While open source intelligence tools can’t prevent ransomware, they can help organizations mitigate the potential damages.
Securing the supply chain
Supply chains can stretch across continents with potentially hundreds of suppliers and manufacturers all around the world bearing responsibility. Should any single part or resource be in short supply, then assembly lines can be brought to a halt resulting in costly delays at the very least.
There are numerous threats to the supply chain, one of which is malware and in particular regard to this article, ransomware. A key example of this is when the shipping giant Maersk had their IT systems taken out by a malware NotPetya. This resulted in their IT systems being down for days and many deliveries being delayed despite Herculean logistical efforts by the company.
Using OSINT tools you can learn whether an organization on your supply chain has been affected by ransomware in real-time which will allow you to take the necessary actions to mitigate the damage this has as their production or logistics is slowed.
Industry Targeting
It’s not unusual for malware to exploit weaknesses which are specific to an industry. For example, the Healthcare industry is particularly susceptible to ransomware as a delay in returning their operations to normal could result in patients deaths. Indeed a leading medical-research institution working on a cure for Covid-19 were forced to pay hackers a $1.14m USD ransom because of a ransomware attack.
Using OSINT tools you can monitor your own specific industry to determine what strategies and exploits are currently being used by cybercriminals against like companies. Determining this will allow you to take extra and specific precautions to fend off similar attacks which could potentially be turned on you.
Detect New Ransomware and Strategies
Cybercriminals are continuously evolving and updating their strategies and the ransomware that go with them. We are unlikely to see the end of this development.
By using OSINT to monitor darknet forums and market places security professionals are able to learn about the newest strategies being employed, the most recent weaknesses being exploited, and the most current software being utilized. Armed with this knowledge they are much more able to develop effective countermeasures as well as actively prevent ransomware infection.
Why a Dark Web Scan is Essential for your Business
With the right tools, like Signal threat intelligence software, monitoring and filtering through information on the dark web is entirely possible without ever needing to download a Tor browser, allowing users to effectively protect their staff, customers and assets.
The dark web is a layer of the internet that is only accessible through an encrypted browsing software such as a Tor browser. This software makes the user anonymous. It is this anonymity which is so beneficial to criminals who are able to trade illegal items and services.
Cybercriminals are known to buy and sell stolen data, for example, which can be used to commit identity theft and fraud. Many of the overtly criminal websites require membership logins that you can only gain if you are active as an online criminal making it challenging for companies and security forces to access and monitor these websites.
However, with the right tools, like Signal threat intelligence software, monitoring and filtering through these websites is entirely possible without ever needing to download a Tor browser yourself.
What is dark web scanning?
A dark web scan monitors open-source information available on the dark web, using both human and artificial intelligence to scan things like criminal chat rooms, blogs, forums, private networks and other sites. In doing this it helps organizations detect potential security threats.
Examples of activities that have been identified from dark web content using Signal Threat Intelligence software include;
Online markets selling stolen and fake goods;
Hackers selling non-sensitive data for use in credential stuffing attempts;
Impersonation of individuals or organizations;
Details in regard to hacking or incitement to hack;
Reputational risk via fake news or impersonation;
Illegal activities such as drugs and drug paraphernalia;
Information regarding a previously undetected sensitive data breach.
What happens during dark web monitoring?
There are some 55,000 dark websites, however, many of these are inactive and even fewer of them are actually used for overtly criminal activity. During dark web scanning our security software monitors and detects any data that is relevant to the particular search queries that have been set up. This allows you to create a customised highly relevant stream of data and information around key points of interest for your company.
The information can also be run through a sentiment filter to create an even further refined stream of data, we explore this in further detail below.
Why is dark web monitoring with Signal Corp important for businesses?
1. Detecting data breaches
Our software has been used to identify stolen credentials and other personal information that is circulating on dark web networks and other channels.
To identify relevant data you are able to set up specific search queries within the software. These constantly monitor the open, dark and deep web and then filter these searches using our AI technology to determine what is and isn’t relevant. We then add a human touch to the remaining data to further filter using human intelligence to identify what is highly relevant.
The scan infiltrates private sites - many of which require membership within the cybercriminal community to enter.
When it comes to detecting data beaches it can quickly identify chat around data that is circulating online which has been gained by illegal hacking attempts. If data is detected from a particular company, whilst there is no way to retrieve that data organisations can take precautionary measures to mitigate the damage and threat of the data breach as well as determining how the data was gained and ensuring that breach is secured against further data beach attempts.
2. Detecting Physical Threats against People and Assets
The big draw for criminals to the dark web is that all users need to use an encrypted browser to access the dark web which entirely anonymises their presence. This means, very simply, that criminals can and do talk about their activity, either to brag or as part of their preparations.
Using software like Signal you can constantly monitor the dark web and when a criminal talks about or potentially threatens one of your staff or assets you can know instantly. Whilst they are anonymised and you won’t know who is planning something, you will know that there is a very real potential threat that you can now guard against.
3. Predicting potential terrorist actions
In the same vein as detecting potential physical threats against a company online, the dark web is also a place where terrorists go to communicate and organise. By monitoring the dark web then you can pick up on their conversation and use the data gathered to potentially predict and deter terrorist attacks aimed at the company.
How do you determine when chat becomes a serious threat?
One of the potential issues some of our customers face is the sheer amount of noise which might surround their brand. Invariably not all of this noise is good. Which is why we have a sentiment analysis tool to help filter out what chat, what noise online we need to pay attention to.
On top of this, this can then closely monitor individuals who have been detected to hold negative sentiments towards a customer and it can determine if that was a once-off comment, or if this negative sentiment might actually evolve into a more palpable threat.
Mitigating the Threat of Data Breaches and the Risks of Credential Stuffing
In this article, we explore a growing concern for a number of businesses which poses increased year on year risk, with increasingly costly repercussions - credential stuffing. Why does it pose a severe security risk? And how can dark web monitoring and social media monitoring be used to mitigate the threat of data breaches?
How are data breaches of non-sensitive data used by cybercriminals?
When it comes to cyberattacks having detailed situational awareness and the ability to quickly sift through open-source data and information on the surface, deep, and dark web allows businesses and financial institutions to quickly determine potential risks and take necessary precautionary actions fast. This can help mitigate threats posed by cybercriminals, reducing the security spending and costs surrounding the fallout after criminals successfully commit fraud through the use of leaked data.
In this article, we explore a growing concern for a number of businesses which poses increased year on year risk, with increasingly costly repercussions - credential stuffing. We answer the following questions and more: what is credential stuffing? Why does it pose a severe security risk? And how can dark web monitoring and social media monitoring be used to mitigate the threat of data breaches?
What is credential stuffing?
Many businesses assume that non-sensitive customer data has little value to a cyber-criminal.
In fact, in a recent study, it was found that a number of businesses didn’t even password protect cloud-stored customer data. Meaning anyone could have come along and downloaded the entirety of those databases.
What is even more worrying, is that many data breaches go entirely undetected.
Credential stuffing is a tactic growing in popularity that weaponises non-sensitive stolen credentials (eg. usernames and passwords) against websites and mobile applications. Large volumes of stolen account logins are tested against other website login pages to gain unauthorised access to accounts, in order to commit fraud.
The most remarkable aspect of credential stuffing is that a given business does not have to be breached itself to suffer from credential stuffing. The vulnerability is simply having a login form and having users.
Whilst the strike rate is low - think a few successes for every thousand attempts - there are billions of stolen credential pairs in the hands of cybercriminals.
In 2018 there were 2.8 billion credentials stuffing attempts reported in the US alone. And this number is only rising. Which goes to show just how much of a threat credential stuffing has become.
On top of this, a skilled hacker, using a throttled bot with multiple Autonomous Systems Numbers (ASNs) and IP addresses can remain undetected for long periods of time, allowing them to try potentially millions of login combinations without anyone knowing anything untoward is happening.
Source: idtheftcenter.org
What are the cybercriminal’s goals?
“It is a misconception that only financial information like payment card numbers or bank accounts has monetary value to data thieves.” - Source
Obviously, the most valuable data for cybercriminals is going to lead them to bank account and credit card details. These they can use directly to access a persons money. In 2019 though, there was a significant decrease in the amount of sensitive data exposed. Going from a reported 471 million records in 2018, down to 164 million in 2019. It’s worth noting though that the Marriot breach in 2018 did skew the records there with over 300 million sensitive records exposed in that single data breach.
However, there are numerous ways a cybercriminal can benefit from accessing another persons account data through credential stuffing of purportedly non-sensitive data. These strategies will be tailored to the sites they gain access to and can lead to various forms of identity fraud and phishing scams.
Part of the reason this indirect strategy is growing in popularity with cybercriminals is that sensitive data is becoming better and better protected by corporations and financial institutes. However, this somewhat simplistic approach creates a serious vulnerability to any company.
Credential stuffing is costing businesses millions each year. Not just in the follow-up costs of a cyber attack and the ramifications of fraud, but from increases inIT security spending, potential lost revenue from lost customers, and application downtime. This, according to one study by Akamai is costing companies an estimated $4 million a year.
Who is most at threat?
When it comes to what this looks like in real life you only have to take a cursory glance at the numbers to have cause for concern. In 2019 it was reported that a total of 869,857,509 records were stolen by cybercriminals in the US - and it’s likely that many more stolen records went either undetected or unreported.
The majority of that data, around 750 million records, was non-sensitive data, that will largely find its way to the hands of cybercriminals who will use it for credential stuffing.
The credential stuffing technique can be used against any company with a login page.
“Up to 83% of people - according to 2018 research - use the same password for more than one account.”
Consumers face growing complexity in password requirements, with various length requirements, plus symbols and numbers - this has actually encouraged many users to find a single password that fits the bill and they’ve then reused that password or variations of it across numerous account logins. This is then paired with a growing number of individuals who have access varying levels of technology and might not know how to best protect their data.
Source: idtheftcenter.org
What can be done to mitigate the threat of credential stuffing?
People are always talking about having better online security but no one ever talks about what happens after a data breach or after being hacked.
As the old saying goes, “hope for the best, but plan for the worst.” A growing number of companies are on the receiving end of cyberattacks and it is leading to an increasing number of data breaches.
Shoring up online and cybersecurity is absolutely vital. However, it may well not be you who is hacked, instead a victim of the credential stuffing technique. One thing to do is to require two-factor authentication. But even this isn’t flawless as the hacker may well have access to that user’s email account as well.
So, what can businesses do to mitigate the growing threat of credential stuffing? Often hackers responsible for the data breach won’t use all the data themselves. Instead, they’ll turn to the dark web where they can anonymously sell the data instead.
This is where threat intelligence software like Signal comes in. Signal allows for users to monitor the dark web without needing a Tor browser. With threat intelligence software like Signal one can do much more than just monitor the dark web though.
Users can set up alerts for keywords and monitor dozens of channels instantly generating alerts for users based on their search queries. What this means is that as soon as leaked data goes up for sale on the dark web - or as soon as anyone talks about purchasing records gained through illegal or forced access to your database you will know.
You can then take precautionary actions to mitigate the potential threat. For example, warning customers of potentially exposed data so that they can secure any logins with the same password, force resetting customer passwords, and reporting the incident to the authorities.
In one recent example, it was found that an employee of a bank, stole over 3 million sensitive records from their company database. They then went away and bragged about it on social media and on various dark web forums (like 8chan). These set off immediate alerts through the Signal system and action was able to be taken, the data was recovered before it changed hands and the employee faced the legal ramifications of their actions.
Because Signal uses open-source data all evidence and information gathered through its channels are able to be used as actionable intelligence.
Related: Black Hat Brags about Bank Hack Signal Could have Spotted
Detect and remedy data breaches fast with Signal
Get in contact to learn more, or request a demo using the options below: info@signalpublicsafety.com
Resources and Further Research
The Power of Emotional Analysis - introducing Signal Spotlight
In 2018 we launched Signal Spotlight! This feature allows users to analyse the emotion behind potential threats to determine associated risk. Signal users get a real-time overview of the emotional state of Signal search results to better understand the emotional drive behind identified threat intelligence.
Signal Spotlight provides a real-time overview of the emotional state of Signal search results. Using Signal Spotlight, Signal users can better understand the prevalence and drivers of emotions and what is happening in real-time.
Spotlight taps into the results from Signal search criteria across many data sources to better understand the prevalence and drivers of emotions. For example, during an incident or event, an important attribute is how people are feeling about what has happened and how the emotional state may be changing real-time as that incident/event unfolds.
The Spotlight underlying technology uses a large vocabulary of emotion terms that were compiled from multiple sources, including the ANEW and LIWC corpora, and a list of moods from LiveJournal. In addition, a crowdsourcing task was run to organise these terms against Parrott's hierarchy of emotions. The emotions are colour-coded using a dataset of affective norms provided by the Center for Reading Research at Ghent University.
Spotlight leverages technology and research undertaken by the Language and Social Computing team in the Digital Economy Programme of CSIRO's Digital Productivity Flagship and originally developed as a joint project between computer scientists at CSIRO and mental health researchers at The Black Dog Institute.
Reference
Milne, D., Paris, C., Christensen, H., Batterham, P. and O'Dea, B. (2015) We Feel: Taking the emotional pulse of the world. In the Proceedings of the 19th Triennial Congress of the International Ergonomics Association (IEA 2015), Melbourne, Victoria, Australia, August 2015.