The Crucial Role of Social Media Monitoring in Corporate Threat Intelligence
An estimated 2.94 billion people globally use social media. This is roughly a penetration of about 40% which is only expected to grow. However, in developed countries, this penetration rate is even higher. Facebook and Instagram are currently the two most used platforms, but there are numerous channels with hundreds of millions of active users daily.
On any one of these channels, attackers might voice their intentions, spread false information concerning your organisation, or partake in more obscure but potentially equalling dangerous activities such as cyber-bullying or phishing. Because of the high number of users paired with the social nature of discussion, potential threats often emerge on these channels and forums first, even before they become a tangible risk.
On top of this, many companies have active social media presences which enable them to engage with their target audiences for positive brand growth. However, because of the saturation, companies are opened to several new vulnerabilities that come hand in hand with the opportunities that social media presents.
A fundamental challenge with social media monitoring, then, is knowing where to look and how to identify credible threats amidst overwhelming noise in a timely fashion that doesn’t require immense resources.
In this article, we explore some of the key threats that evolve and can be monitored using social media channels as well as how to overcome the fundamental difficulties surrounding effective social media monitoring.
The Challenges of Social Media Monitoring
Using social media monitoring as part of your comprehensive cybersecurity strategy has several key benefits unique to the platforms involved. However, leveraging social media for increased security and situational awareness can be a challenge and, without the right tools, it is next to impossible to effectively monitor these channels and form timely responses.
The amount of chatter on social media channels is both a boon and a curse to security professionals. People discuss everything from the inane to clearly threatening conversations and actions. All of this happens though, across dozens of social media channels. On Twitter alone, there are some 500 million tweets a day. In one study, it was found that five new profiles are created on Facebook every second - and it’s quite possible that some of those are fake or could be a threat to your business.
An example of using social media to gain increased situational awareness is the 2019 Christchurch shooting. Parts of the event were live streamed through social channels. Those security teams monitoring these channel were amongst the very first to know of the event as well as gain valuable situational awareness that allowed them to respond more effectively than without this information.
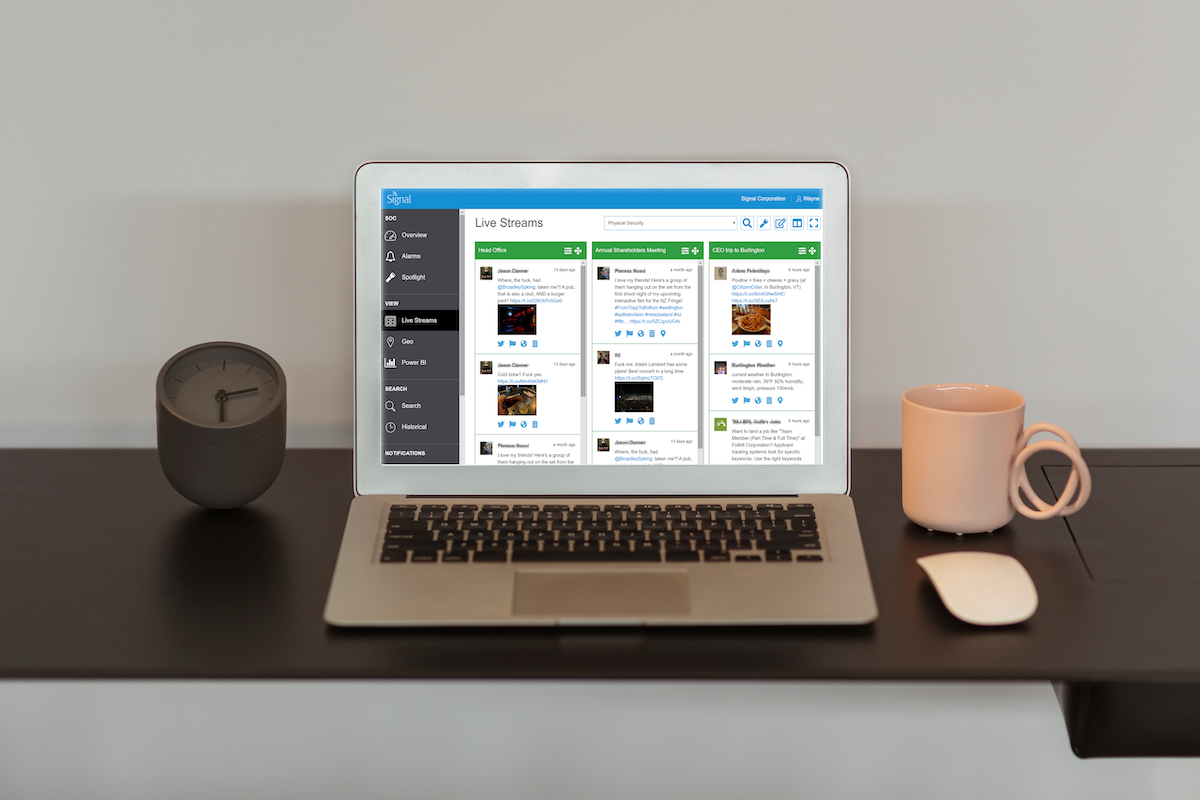
To overcome the key challenges presented by social media monitoring it is vital to employ the right tools and resources. For example, Signal OSINT platform allows you to monitor your chosen social media channels continuously and set up tailored lives streams and customised filters to help user identify potential threats from the noise of online chatter. To further refine the data gathered through the use of Signal you can run things through our sentiment analysis tool.
Signal enables users to monitor not just social media but the surface, deep, and dark webs in their entirety forming the crux of many organisations’ security efforts.
Identifying Threats
Intertwined in the comments, posts, pins and tweets are a multitude of information security and business risks. From targeted phishing to full-on account takeovers or even emerging threats against physical assets. As social media continues to dominate business communications, security teams must understand and address the risks posed by social media, the largest unsecured IT network on earth.
Here are a few of the key identifiable security threats associated with social media.
Targeted Phishing
Phishing attacks have been evolving over the years to incorporate and take advantage of the everyday tools that both businesses and consumers use. One such method is by using social media to gather data on targets through phishing attacks and other strategies.
For example, is your mother’s maiden name listed on your Facebook? Where did you go to school? Did you post pictures of your first ever pet? All of this data commonly used for security questions is freely available for determined fraudsters. For those that are a little more enterprising, they might even get you to volunteer particular details disguised as a fun quiz. Phishing attacks are generally used to gain valuable data which can then be used for monetary gain.
Social Engineering
By using social platforms criminals can build trust and through the use of deception manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes. This can take on several different aspects whether it’s targeting employees to divulge information about a company or manipulating customers to share personal information that would allow them login access to their accounts for the purposes of identity fraud.
Account Takeover
An account takeover is a form of identity theft. This is when fraudsters illegally use bots to gain access to a victims account. There are several reasons this could be valuable to a hacker. For example, what they might do is launch a phishing attack from this account which will allow them to utilise the trust associated with that individual’s personal account to increase the chances of success.
Physical Threats
Social media is a public forum where a huge number of people go to express their opinions. What this inevitably means is that both positive and negative sentiment is expressed about companies, organisations and people. Some of this sentiment holds serious reputational risks or may even evolve into a serious physical threat against an employee or asset.
Final Words
Experienced hackers and cyber-criminals, understanding the public nature of the channels will attempt to avoid actions that expose their intentions. Social media threat monitoring in this way has its limitations, which paired with those relating to privacy protections inhibit it from being a comprehensive intelligence source.
That being said, social media, when monitored effectively can catch negative sentiment as well as expose potentially dangerous or threatening information or conversations in real time - some of which will prompt further investigation or other actions to be taken. Social media monitoring can provide critical real time information on threats increasing situational awareness, but organisations and their security teams are well-advised to not lose sight of the forest for the trees.
The usefulness of social media monitoring is best leveraged in a holistic risk management approach, one that incorporates diverse security strategies, including a range of cyber security measures.