Threat Intelligence for Communications and Technology Companies
Remaining aware of the litany of evolving threats that could be and are currently being perpetrated against communications and technology companies is a priority if they want to have any hope of defending themselves against cyber or physical threats.
Communication and technology companies form an integral part of the daily activities of many individuals, companies, and governments. This sector forms a foundation of critical infrastructure which is in part what makes it such an appealing target for cybercriminals.
A successful cyberattack on a company in this sector could see vital services for hundreds of thousands if not millions disrupted. A severed internet connection could see businesses crippled and potentially shut down entire governments.
Remaining aware of the litany of evolving threats that could be and are currently being perpetrated against communications and technology companies is a priority if they want to have any hope of defending themselves against cyber or physical threats.
Telecom operators are adept at protecting their networks, additionally, with the telecom infrastructure being the primary transport for most attacks it’s also true that cybercriminals also have to rely on this infrastructure. This limits the adversaries who directly attack telecom infrastructure largely to anti-establishment hackers.
However, today, telecom organisations are recasting themselves as technology companies - which is why this article encompasses both. For instance, they are creating mobile applications for use of VoIP calls and storing data on cloud services. The lines between technology and communications companies become even more blurred with large tech companies owning parts of the infrastructure as well as those tech companies which have crossed over into the realms of communications. Apple, Facebook, and Google being the most obvious examples.
This cross-over between communications and technology creates new risk frontiers for both communication and technology companies.
“One mounting technology concern is Internet route hijacking, also known as IP hijacking, an exploit in which adversaries corrupt Internet routing tables to ‘hijack’ packets of data. Possible solutions include the implementation of secure Border Gateway Protocol (BGP), a technology that can be used globally. However, secure BGP standards haven’t been consistently adopted, and that’s not likely to happen without government incentives.”
In addition to the growing number of cyber threats, it’s also necessary to consider threats against executives as well as supply chain vulnerabilities which might be exploited. The fact that many of large organisations operate internationally, where materials and equipment manufactured in various different parts of the world is the final part of an ever-evolving ecosystem of threats.
Threats Facing Technology and Communications Companies
Today’s cybercriminals are evolving and adapting fast, discovering and creating new vulnerabilities to exploit constantly. Addressing these threats requires telecommunications and technology companies to have access to up-to-the-minute knowledge and information about threats and vulnerabilities for a vast array of potential attack vectors.
We can divide the main threats facing the communication and technologies industries into two interrelated categories:
Threats targeting companies directly.
These include DDoS attacks, targeted attacks (APT campaigns), network device vulnerabilities and human-related threats like insider access, social engineering and the risk of allowing third parties to access information.
Threats targeting subscribers of services.
Particularly the customers of cellular service providers (CSPs) and Internet service providers (ISPs). These include malware for mobile devices, subscriber data harvesting, end-user device vulnerabilities, and more.
Mobility and the Cloud
Another key issue for these industries is the proliferation of smartphones and internet-capable devices. Despite this being a pressing concern it has been found that technology and communications companies have done little to deploy security measurements with only around 45% of organisations having a mobile device security strategy in place.
As the use of mobile devices increases so does the use of cloud computing services. The cloud has been around in its modern context since at least 2006 however, it is becoming increasingly used by modern organisations with some today 50% of operators currently using some sort of cloud service.
The use of the cloud opens up new business growth avenues and increasingly optimises workflows allowing individuals to work and manage their data from anywhere on any device. However, it simultaneously creates new attack vectors which are compounded by the use of mobile devices.
Whilst organisations share increasingly more data with third parties, vendors, partners, and customers it has been found that a striking lack of security practices exists for IoT and cloud-enabled devices.
67% had an IoT security strategy.
34% had policies for secure collection, retention and destruction of new data.
36% had implemented uniform cybersecurity policies across all IoT devices and systems.
How Communications and Technology Companies are Improving Cybersecurity
Security is everybody’s business. Any member of staff might be exploited as a weakness. In a 2018 survey it was determined that 30% of security incidents were attributed to an employee compared to 23% attributed to an external hacker and 19% attributed to third party vendors. Employees could become threats in a variety of ways, accidentally or maliciously.
For example, they could be personally hacked and extorted for access to protected data. Or they could be a victim of a phishing attack unwittingly installing malware on company devices allowing hacklers to steal packages of data. Or, it could be a location or particular executive that is physically targeted for an attack. The variety of dynamic threats means that it’s not just security teams that need be involved in and informed about threats.
One trend that is true across industries including telecom and technology companies is an increased budget for cybersecurity and threat intelligence.
“It’s predicted that global spending on cybersecurity products and services will exceed $1 trillion cumulatively over the five-year period from 2017 to 2021.”
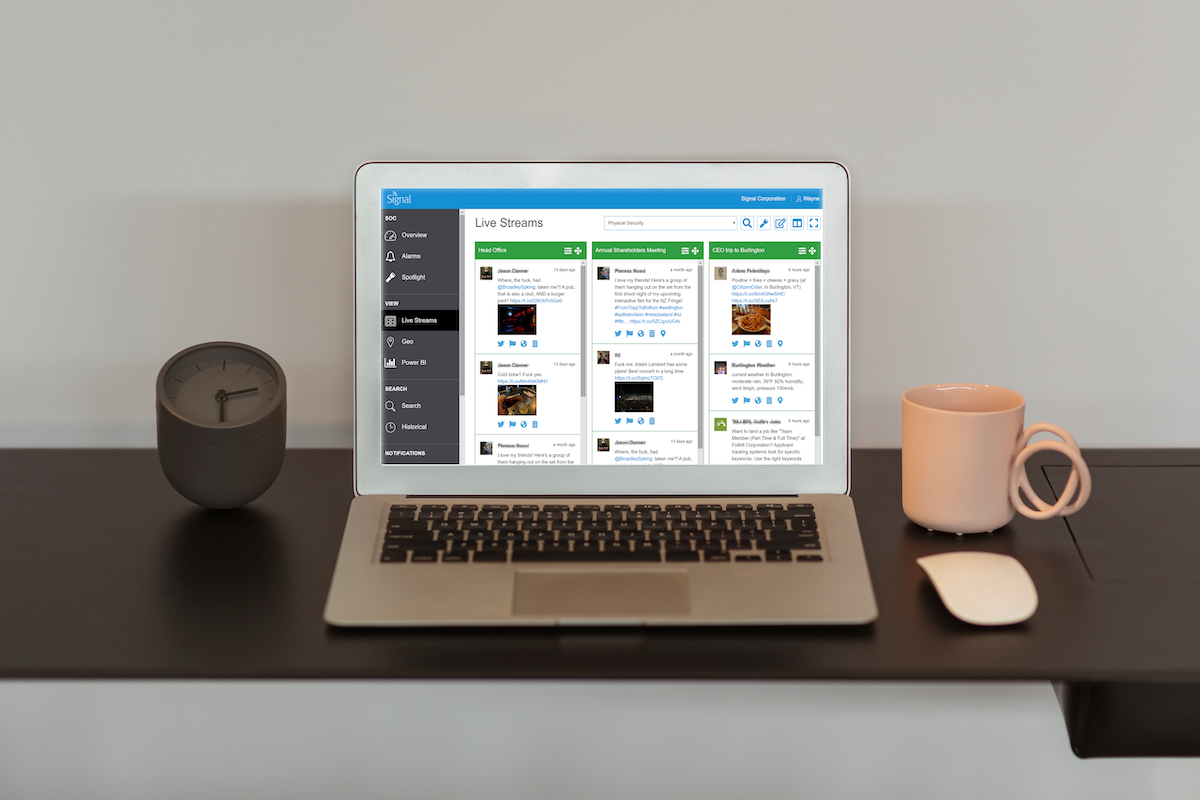
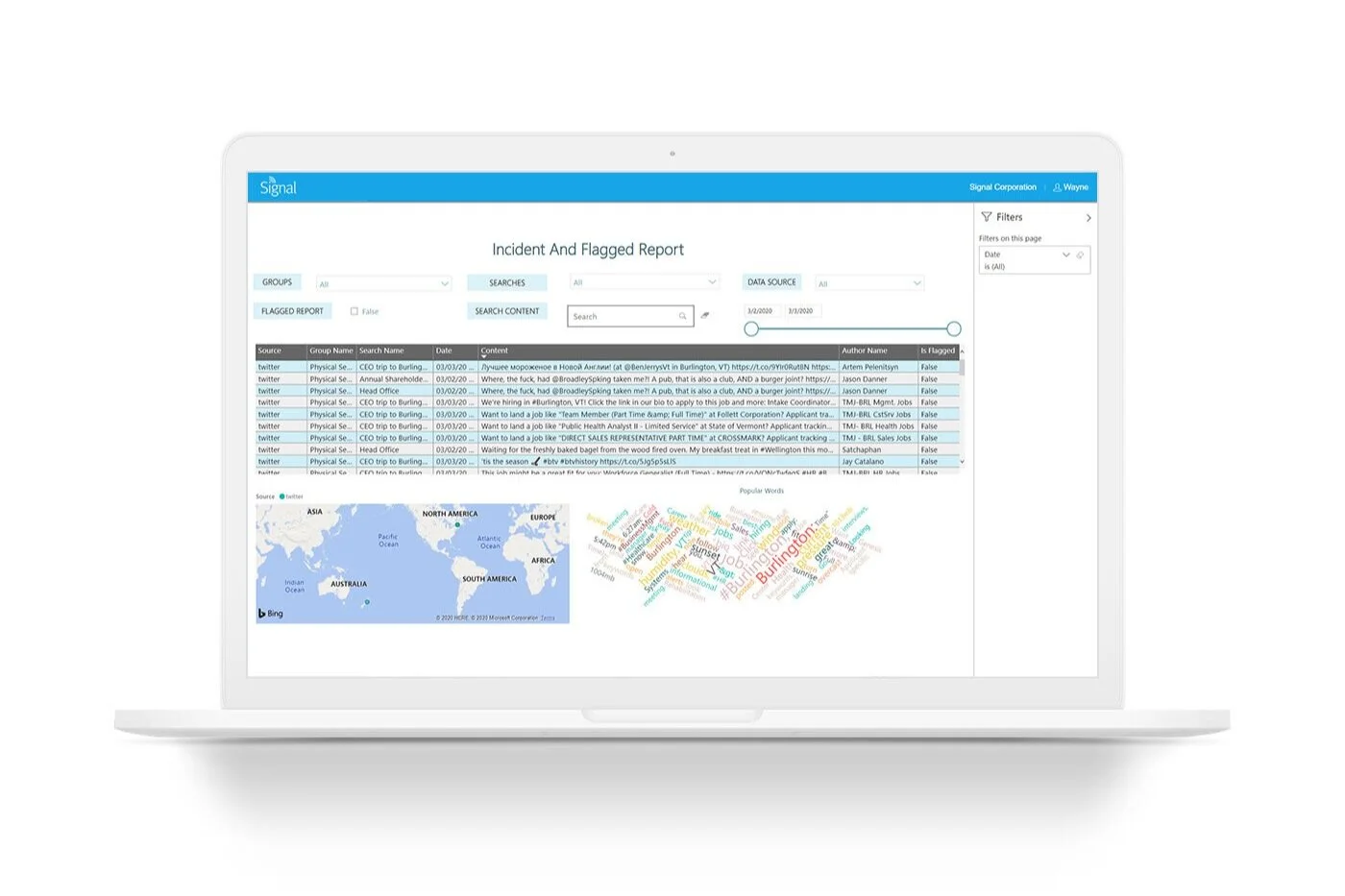
Another measure is an increasing focus on intelligence. Threat intelligence using tools like Signal allows organisations to efficiently obtain hyper-relevant data in real-time.
How is Signal being used today to protect organisations?
Company data is discovered for sale on the dark web.
Threats to an office location are found in online discussion forums.
Signal discovers an employee sharing sensitive company information online.
Final Words
Today, information security is an advanced discipline that requires the correct technology and processes paired with a skillset based on counterintelligence techniques and supported by top executives. As technology evolves new threats will inevitably appear along with a raft of new challenges.
For companies to mitigate the risks presented by an evolving threat landscape core practices such as employee security training need to be reassessed and continuously updated based on the newest information. The convergence of mobile technology, cloud services and social networking have multiplied risks - and many operators have yet to address many of these increased vulnerabilities.
These factors call for a new approach to security, one that’s driven by the knowledge of threats, assets, and adversaries. One in which security incidents are seen as a critical business risk that may not always be preventable, but can be managed to acceptable levels.
The Role of Threat Intelligence and Cybersecurity in Retail
The rise of e-commerce and the adoption of digital technologies has opened up a number of new security risks for the retail industry. Hackers who manage to take advantage of any of these attack vectors can do a lot of damage to both a companies bottom line and reputation. Which is why it's more important than ever for businesses to employ the right tools to protect their people, data, and assets.
Retail is the fourth most targeted industry by cyber-criminals. It is the same technologies that have created new potential growth opportunities for these businesses which has simultaneously opened up new and evolving attack vectors for both cyber-criminals and physical attacks.
Use of the cloud, IoT (Internet of Things) and global expansion increases potential risks exponentially, as these threats are no longer constrained by location or borders. Organisations need to secure customer data, protect executives, manage travel, predict physical threats to assets, and prevent cyber-attacks. All of these threats could come from a range of possible sources involving a plethora of evolving methods, from anywhere in the world.
Digital and In-Store Locations Are Both Valuable Targets
Retailers deal with large numbers of people. As such, their databases necessarily contain vast amounts of data which could be valuable to hackers. This includes but isn’t limited to personally identifiable information (PII) for customers, employees and even executives. Vulnerable PII which contains financial information is highly valuable and the most obvious of targets for hackers, however, even non-sensitive data can be a hugely profitable attack vector for cyber-criminals when used correctly. This is shown by the frequent sales of login credentials on the dark web.
Additional avenues of attack include mobile retailer apps, customer-facing devices in retail locations, and IoT product offerings. These new technologies are continuously assessed by cybercriminals for potentially exploitable weaknesses and can often be found mentioned in online discussion forums. Because of this, public-facing social media data, as well as data collected off the dark web, is more valuable than ever in detecting threats.
Social media, as well as anonymous forums on deep and dark websites, are used to discuss or advertise criminal strategies like shoplifting, POS fraud, and counterfeiting. Public-facing social media data is more relevant than ever for detecting sentiment, executive threats, and critical events like active shooters in or around retail locations.
The Heavy Cost of Threats for Retailers
The cost associated with the risks outlined in this article are huge. Retail inventory loss incurred by shoplifting or fraud costs the industry an estimated $50 billion a year. The average cost of a data breach, according to a 2018 Ponemon Institute report, is USD $3.86 million. And these are just the measurable costs. The long lasting effects that comes with the reputational damage and global brand erosion that coincides with a data breach that exposes customer or executive data is also a highly valid concern.
This information points to the importance and necessity for an effective data discovery and analysis programme to be employed by companies to effectively secure organisations in the retail industry. Security teams are burdened with a seemingly impossible task of processing an ever-increasing and varied amount of threat data to separate the noise from the real threats to contextualise that data into actionable insights. This industry needs tools that automate and accelerate data analysis to enable effective threat monitoring and prediction.
- 50% of retailers have experienced a data breach.
- 84% plan to increase IT security spending.
- 85% of retail IT security professionals said their organisation used cloud storage for sensitive data.
The Importance of Cybersecurity in Retail
The rise of e-commerce and the adoption of digital technologies means that retailers now hold vastly more data on their customers than ever before. Most major outlets currently have online stores and it’s expected that online sales will outstrip high street sales within the decade. Gaining access to customer accounts can give access to PII and even bank details. Hackers who manage to obtain this customer data will either use this data themselves or more likely sell it on the dark web.
One of the popular methods that this data is used for is an approach called credential stuffing. This attack works because many customers use the same login credentials across many different sites. Hackers will take these credentials and make multiple automated login attempts across an array of websites. One team of security analysts found that 90% of retail login attempts were from hackers attempting to access other people’s accounts in this way.
Another common attack vector is payment processes. Retailers are embracing technology to make it as easy as possible for customers to purchase through their online stores, however, if security standards aren’t advanced alongside these payment processes then they leave vulnerabilities to fraudulent activity.
A final key cybersecurity vulnerability for retailers is the staff. Often retailers hire young and inexperienced staff, most of whom have had little if any cybersecurity training. This leaves them vulnerable to common ‘social engineering’ attacks such as ‘phishing’. For example, a hacker might contact a staff member directly and trick them into installing malware onto a company device or attempt to get them to provide sensitive information by pretending they are someone that they aren’t.
Additional Threat Vectors for the Retail Industry
A few examples of additional threat vectors that the retail industry need to pay careful attention to include:
Gift card cloning
In a 2018 report security firm Flashpoint identified found hundreds of discussions of "cracked" gift cards on criminal web forums.
There are several strategies to hack gift cards. One example is by predicting the gift card numbers, which when combined with a brute force attack, means hackers can identify activated cards and the amounts on them. Another method involves creating clone cards of inactive gift cards and then when they are activated using the credit before the rightful owner has a chance.
Whichever method they choose it’s often the retailer that’s left picking up the tab.
Executive and employee threats
As with any industry, staff may be targeted, not just for phishing attacks or fraud but for physical attacks by disgruntled customers or even terrorists.
Threats to physical locations
From active shooter attacks to terrorist assaults physical locations, especially those where members of the public can come and go freely, are high-risk locations.
By utilising the right technology companies can identify threats early and mitigate the potential damage by forming an effective response based on real-time data fast.
What modern security means for modern retail
Criminals can leverage the web to commit both physical (such as in-store theft), as well as cyber-attacks (such as phishing or gift card cloning). This leaves retailers operating in a unique threat landscape with a broad array of potential attack vectors.
There are three levels that modern retailers should consider to ensure a complete and effective security, both in-store and online. First, at the highest level, training and information need to be gathered for both their security teams, both also disseminated to employees across the organisation so that everyone is aware of the threats and how to avoid them.
The next level is to only work with secure third-party providers. Companies that take security seriously and when it comes to building defences against cybercrime have strong records. These businesses, such as connected devices, cloud storage or payment portal providers form a crux of any companies security.
Finally, the security team need to be enabled with the right tools for the job at hand. Signal OSINT software enables security teams to scan a vast number of open, surface, and dark web channels and sources to gain real-time data on emerging threats. Our sentiment analysis, custom filters and advanced alerting means security teams can be notified instantly on threats as they are emerging. Whether it’s customer data for sale online, or an active shooter situation in-store, security teams can quickly assess and respond to mitigate risks and damages.
The Crucial Role of Social Media Monitoring in Corporate Threat Intelligence
We explore some of the key threats that corporate security teams monitor through social media channels as well as how to overcome the fundamental difficulties surrounding effective social media monitoring.
An estimated 2.94 billion people globally use social media. This is roughly a penetration of about 40% which is only expected to grow. However, in developed countries, this penetration rate is even higher. Facebook and Instagram are currently the two most used platforms, but there are numerous channels with hundreds of millions of active users daily.
On any one of these channels, attackers might voice their intentions, spread false information concerning your organisation, or partake in more obscure but potentially equalling dangerous activities such as cyber-bullying or phishing. Because of the high number of users paired with the social nature of discussion, potential threats often emerge on these channels and forums first, even before they become a tangible risk.
On top of this, many companies have active social media presences which enable them to engage with their target audiences for positive brand growth. However, because of the saturation, companies are opened to several new vulnerabilities that come hand in hand with the opportunities that social media presents.
A fundamental challenge with social media monitoring, then, is knowing where to look and how to identify credible threats amidst overwhelming noise in a timely fashion that doesn’t require immense resources.
In this article, we explore some of the key threats that evolve and can be monitored using social media channels as well as how to overcome the fundamental difficulties surrounding effective social media monitoring.
The Challenges of Social Media Monitoring
Using social media monitoring as part of your comprehensive cybersecurity strategy has several key benefits unique to the platforms involved. However, leveraging social media for increased security and situational awareness can be a challenge and, without the right tools, it is next to impossible to effectively monitor these channels and form timely responses.
The amount of chatter on social media channels is both a boon and a curse to security professionals. People discuss everything from the inane to clearly threatening conversations and actions. All of this happens though, across dozens of social media channels. On Twitter alone, there are some 500 million tweets a day. In one study, it was found that five new profiles are created on Facebook every second - and it’s quite possible that some of those are fake or could be a threat to your business.
An example of using social media to gain increased situational awareness is the 2019 Christchurch shooting. Parts of the event were live streamed through social channels. Those security teams monitoring these channel were amongst the very first to know of the event as well as gain valuable situational awareness that allowed them to respond more effectively than without this information.
To overcome the key challenges presented by social media monitoring it is vital to employ the right tools and resources. For example, Signal OSINT platform allows you to monitor your chosen social media channels continuously and set up tailored lives streams and customised filters to help user identify potential threats from the noise of online chatter. To further refine the data gathered through the use of Signal you can run things through our sentiment analysis tool.
Signal enables users to monitor not just social media but the surface, deep, and dark webs in their entirety forming the crux of many organisations’ security efforts.
Identifying Threats
Intertwined in the comments, posts, pins and tweets are a multitude of information security and business risks. From targeted phishing to full-on account takeovers or even emerging threats against physical assets. As social media continues to dominate business communications, security teams must understand and address the risks posed by social media, the largest unsecured IT network on earth.
Here are a few of the key identifiable security threats associated with social media.
Targeted Phishing
Phishing attacks have been evolving over the years to incorporate and take advantage of the everyday tools that both businesses and consumers use. One such method is by using social media to gather data on targets through phishing attacks and other strategies.
For example, is your mother’s maiden name listed on your Facebook? Where did you go to school? Did you post pictures of your first ever pet? All of this data commonly used for security questions is freely available for determined fraudsters. For those that are a little more enterprising, they might even get you to volunteer particular details disguised as a fun quiz. Phishing attacks are generally used to gain valuable data which can then be used for monetary gain.
Social Engineering
By using social platforms criminals can build trust and through the use of deception manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes. This can take on several different aspects whether it’s targeting employees to divulge information about a company or manipulating customers to share personal information that would allow them login access to their accounts for the purposes of identity fraud.
Account Takeover
An account takeover is a form of identity theft. This is when fraudsters illegally use bots to gain access to a victims account. There are several reasons this could be valuable to a hacker. For example, what they might do is launch a phishing attack from this account which will allow them to utilise the trust associated with that individual’s personal account to increase the chances of success.
Physical Threats
Social media is a public forum where a huge number of people go to express their opinions. What this inevitably means is that both positive and negative sentiment is expressed about companies, organisations and people. Some of this sentiment holds serious reputational risks or may even evolve into a serious physical threat against an employee or asset.
Final Words
Experienced hackers and cyber-criminals, understanding the public nature of the channels will attempt to avoid actions that expose their intentions. Social media threat monitoring in this way has its limitations, which paired with those relating to privacy protections inhibit it from being a comprehensive intelligence source.
That being said, social media, when monitored effectively can catch negative sentiment as well as expose potentially dangerous or threatening information or conversations in real time - some of which will prompt further investigation or other actions to be taken. Social media monitoring can provide critical real time information on threats increasing situational awareness, but organisations and their security teams are well-advised to not lose sight of the forest for the trees.
The usefulness of social media monitoring is best leveraged in a holistic risk management approach, one that incorporates diverse security strategies, including a range of cyber security measures.
4 Aspects of Effective Executive Travel Risk Management
Businesses have begun realising the importance of reducing travel risks especially for executives where the potential of risk is increased and the potential cost heightened. Signal risk intelligence software enables users to monitor the surface, deep, and dark web to better protect people and assets.
All organisations want to keep their employees safe, this goes across the supply chain and up to top executives. Whether they’re protecting them from the likes of terrorism, upset customers, natural disasters or road accidents, these risks are heightened when employees and especially executives travel.
Whilst threats to travel security are not limited to highly unlikely events, many serious threats like the sudden eruption of a volcano, or terrorist are, thankfully, things that most travellers never have to worry about. However, if COVID-19 has shown us anything it’s that no matter how unlikely a situation may be, they are still a possibility and could escalate incredibly quickly.
Businesses have over the last years begun realising the importance of reducing travel risks especially for executives where the potential of risk is increased and the potential cost heightened. In a 2017 study by Business Travel News of 229 travel buyers and managers and corporate safety and security managers, it was found that “65% said their companies' attention to traveller safety and travel risk management has increased over the past three years.” Ignoring the risks that travel holds could be an expensive mistake.
4 Essentials to Consider for a Effective Travel Security
Reliable Intelligence
Education
Briefings
Planned Response
Reliable Risk Intelligence
Without an accurate risk assessment and a detailed understanding of the potential local risks, a security team cannot make a properly balanced decision regarding operation security. It is incredibly important then, not just for teams to perform risk assessments before travel but to continually monitor local situations so that should things change the security team can react accordingly and take appropriate actions.
For example, as COVID-19 was evolving into a global pandemic security teams needed reliable information from trustworthy sources to allow them to properly understand the potential risks it posed as well as to navigate through the plethora of misinformation being spread. Teams using Signal OSINT were able to get this information and take preventative actions, putting secondary measures into place should the situation evolve. In this particular example, extreme action was needed. The security teams first suspended all executive travel to badly affected areas and as the situation evolved into a more serious global crisis they evacuated executives and employees who were overseas, before entirely suspending further business travel.
Without the proper information, the best course of action cannot be pursued. Situations change rapidly and timely intelligence will provide detail on current and future anticipated threats.
Staff Education
As part of an effective travel security program staff need to be aware of the potential dangers and have the tools and knowledge to minimise and mitigate personal travel risks. Risk can be dramatically reduced with good basic personal security methodology which is often the most cost-effective and efficient way to improve the safety of employees abroad.
Part of this education must be an ongoing effort to share with the relevant parties this real-time information from data sources gathered through tools such as Signal.
Debrief
With properly trained staff, the individuals travelling should be aware of the environment, threats and risks that they are entering. On top of this, as we mentioned above this information sharing should not stop at the briefing, but as the threats evolve the relevant individual needs to be kept up to date so that they can change their behaviour if necessary.
A Planned Response
The fourth aspect of an effective travel risk management plan is having planning a response to all possible crises. In certain locations, some aspects and threats are more prevalent.
For example, emergency services might be lacking or public transport might be more dangerous. In these cases, proper plans need to be put in place. For the latter, you might arrange a rental car for your executive, or a driver, if the road laws are known to be difficult. These preventative actions remove several potential threats which would be far more costly for the business than the cost of something like a driver.
There must be a pre-identified and rehearsed service in place to ensure an effective and timely response to an emergency.
Three main parts to an effective response include:
1. Prevention – The best security avoids or prevents threats from becoming risks. A good benchmark is to be able to identify the exact location of your employees and be able to effectively communicate with them within 15-20 minutes of an incident occurring.
2. Crisis Management – If a crisis does happen, the first thing you need is an effective communications channel. Through this, you need to be able to quickly implement plans and processes to manage the evolving crises.
3. Evacuation or Hibernation Plans – If a situation escalates beyond a certain point it may be that security teams need to implement and evacuation or hibernation plan. Which will either have the executive returned home, or hibernate in-situ until the situation changes. An example of a necessary evacuation plan being implemented would be in response to the Corona Virus. With only a little warning it became apparent to those organisations who had teams or individuals in Wuhan China that they needed to get them out of their fast. This situation then escalated rapidly to become a global crises.
Challenges
Travel security and executive protection comes with a number of challenges. It doesn’t look good to put a large amount of money into executive protection, however, there needs to be a balance to avoid potential risks. If an executive is attacked, or involved in an accident whilst abroad then shareholder value may drop, potentially for days, and sometimes the pressure in these scenarios can have negative effects long after the incident.
A situation can change rapidly, requiring a different response even as soon as hours later., which is why having real time intel of an event is so crucial. With the right systems in place and the right tools in the security teams toolbox, threats can be identified, monitored, and effective preventative measures and contingency plans put in place. All of this acts to protect both the individuals and the company involved.
The Role of OSINT in Managing Executive Safety During Travel
The modern workforce is more decentralized than ever. As employees travel or work remotely, it is important to know about potential issues that could impact their safety and security. Signal can assist with early warnings of:
natural disasters in or near destinations;
potential travel disruptions;
terror attacks;
security threats;
political or economic indicators.
Signal Open Source Intelligence software allows you to gather real-time data. More importantly Signal allows users to tailor their feeds to get customised data relevant to their particular situation. Which means instead of having to monitor every part of the web manually you can instead get customised filtered alerts.
On top of this, Signal risk intelligence software enables users to monitor the surface, deep, and dark web. Many dark web forums don’t allow strangers to access their sites and require authenticated logins which makes it even harder to gain access on to these sites and monitor potential risks that occur in these places which security teams need to be aware of such as data breaches, threats of physical attacks and terrorism.
Learn more about how Signal can improve your executive protection…
Vital Protection for the Healthcare and Pharmaceuticals Industry
Some common threats that management and security professionals in the healthcare industry battle with Signal include fake drugs for sale online, sensitive data leaks, and illegal impersonation of healthcare professionals.
Signal is an Open Source Intelligence tool which is used across a number of sectors to help executive and security teams form efficient and effective responses to emerging and evolving threats to assets and people - both staff and customers.
Some of the ways this manifests is in things like quickly identifying data breaches, allowing users to better protect their customers from threats like credential stuffing. Or through social media monitoring to identify sentiment which could affect a businesses reputation or evolve into a physical threat against an executive.
In short, Signal provides relevant, actionable, and real-time information and tools to monitor multiple online data sources with a simple, easy-to-use interface. We empower security professionals around the world to quickly identify emerging threats, receive real-time alerts, and monitor developing situations in order to save time and resources, protect staff and customers, and manage operational risk.
Why use Signal in the Healthcare and Pharmaceutical Sector
Management and security professionals in the healthcare industry have particular needs when it comes to protecting assets, staff, and patients. Some common threats include fake drugs for sale online, sensitive data leaks, and illegal impersonation of healthcare professionals.
To prevent the afore mentioned risks and others from evolving into tangible threats healthcare professionals in charge of security need to remain vigilant. Having Signal OSINT software in their toolbox allows them to monitor the dark web for leaked data, scan social media for negative sentiment and monitor other sources to detect threats early.
Private medical data leaks
One of the most worrying things may healthcare institutes have to worry about is hackers targeting sensitive patient data. It is estimated that 24% of dark web vendors offer access to the healthcare vertical market. Over recent years there a has been a resurgence in ransomware and phishing attacks targeting hospitals, medical practices, and nursing homes.
The reason these institutes are so attacked is that digital medical data sets are incredibly rich PPI sources. These records are worth a lot on the black markets of the dark web. Having someones personal medical history allows fraudulent claims and identity theft. It’s important to remember that hackers are trying to generate a positive cash flow from their attacks.
It’s not just medical records then that hackers can get out of a medical institutes system. Often there are non-sensitive login pairs as well as payment and credit card details. Which makes this a gold mine for hackers.
Fake drugs for sale online pharmaceuticals online
The WHO estimates that 50% of the drugs for sale on the internet are fake. Due to the high price of some medications there is ample opportunity for false online vendors to take advantage of the customers need. Often the fake drugs are portrayed as the real thing, but at a massively discounted rate.
Pharmaceutical IT security needs to locate and identify these dangerous sites so that they can be shut down in an effort to protect consumers from potentially harmful fake drugs. It’s also important to identify fake online vendors who might be impersonating a companies brands. This could cause both dangers to customers, but also creates a reputational risk for pharmaceutical companies.
Stopping the Spread of Misinformation
In light of the rapid spread of information following the pandemic outbreak of COVID-19, it has never been more clear that organisations need reliable accurate sources of information. Examples of unqualified individuals selling miracle cures, or spreading misinformation for some other reason can quickly spread through the internet. Trustworthy healthcare institutes and sources need to identify and combat this misinformation fast.
How Signal is currently being used to help healthcare professionals
An individual impersonating a doctor was discovered online
The individual was selling fake drugs to customers using their persona as a healthcare professional to give out medical advice and push the sales of fake drugs. By using Signal this threat was discovered and action is taken to prevent further damages.
fake prescription drugs found online
Several examples have been discovered by Signal customers of their drugs online from unofficial vendors. Upon closer inspection, these drugs were not theirs but fake replicas. Signal was used to closely monitor dark web forums where these drugs were for sale as well as fake sites on the surface web where they were more openly available to customers. Using customised searches the fake prescription drugs were quickly located and the threat to customers and the companies reputations removed.
Discovered sensitive leaked patient information.
After a system hack, a healthcare institute using Signal was able to identify some of their patient’s records for sale on the dark web. Whilst the data can’t be retrieved, with this knowledge preventative measure can be and were put in place to minimise the risk of these data sets being fraudulently used.
Threats against staff are uncovered from dissatisfied patients
By using Signal’s sentiment analysis tool, Spotlight, users can determine the emotions behind posts to determine whether or not posts deserve further analysis or attention. This helps users cut through the noise.
Dangerous misinformation caught being spread about COVID-19
Using Signal a dangerous piece of misinformation about COVID-19 was identified. It was particularly harmful as it was being portrayed as an internal hospital memo however, upon inspection the information whilst believable was entirely incorrect. By identifying the misinformation that was being spread healthcare professionals were able to counter with verified and accurate information.
Summary
Signal is an open source intelligence platform that enables efficient monitoring of content in blogs and posts on the surface, deep, and dark web. This allows users to detect and identify potential threats to their business, customers, and assets and then establish effective preventative measures to protect against those threats.
How to tell when negative sentiment becomes a threat to your business
Determining online sentiment doesn't just allow you to understand better how your brand is performing and how people feel about your business though. It can also be used to manage crises and spot potential threats to assets or staff.
Without sentiment analysis, data can be misleading. Sentiment gives data extra context which allows it to be better understood enabling a more effective and accurate response to the potential threat.
There are some 500 million tweets and over 4 million new blogs posted every single day. Each of these sparks another conversation which could house potential threats against an organisation. And we haven’t yet mentioned Facebook, Instagram, Reddit, Flickr, Medium or any of the other dozens of social sites and forums where people post online. And if you thought that was a lot of noise you have to remember the dark web too, where many cybercriminals go to engage in nefarious activities with the protection of a Tor browsers anonymity.
The point here is that the internet is full of noise. Monitoring all of that and then cutting through the noise to detect relevant potential threats requires the right tools.
What is Sentiment Analysis?
Determining online sentiment doesn't just allow you to understand better how your brand is performing and how people feel about your business. It can also be used to manage crises and spot potential threats to assets or staff.
Without sentiment analysis, data can be misleading. Sentiment gives data extra context which allows it to be better understood enabling a more effective and accurate response to the potential rtisks.
It also allows you to differentiate between when a negative comment is simply that, a negative comment, or when it needs more serious attention because, for example, it’s evolving into a physical threat.
Where and How do we Measure Sentiment?
Any text that gets highlighted by Signal OSINT software can be run through our sentiment analysis tool, Spotlight. This allows users to reduce the amount of noise and focus on the threats.
Sentiment can be expressed anywhere online, this might be through social media, in the comments of a blog or even in a dark web forum. Signal allows you to gather data from a huge array of open intelligence sources including (but not limited to) social media and dark web forums.
How can Sentiment Analysis Be Used for your Business?
Emerging Threats
Sentiment analysis can be an incredibly useful tool for those that wish to identify potential risks which might evolve into tangible reputational or physical threats against, employees, executives, brand or assets.
Managing Reputation
Your brand’s health and reputation are important. Having a tool that allows you to analyse the overall sentiment towards your brand and associated keywords gives organisations a bigger and better overall picture of their brand which can be a game-changer for launches of major events or analysing the success of a large marketing campaign.
Evolving Crises
When it comes to dealing with current and evolving crises having up to date and detailed situational awareness, gained through an OSINT tool such as Signal can make a huge difference. However, as we have mentioned before, there is a huge amount of noise out there. So, how do you determine which comments, which posts are relevant and need monitoring?
The answer is to use Signal to create specific filters and then run identified posts through our sentiment analysis tool “Spotlight”. This allows users to both quickly identify emerging threats and to then stay on top of these risks as they are evolving in real time.
Moving Your Marketing Forward
Social sentiment is a powerful tool for understanding the relationship between your brand, your customers, and your competitors. If you measure it regularly and act on what you learn, your team can create targeted marketing strategies to keep up with the ever-changing demands and opinions of your customers.
How do you determine when Negative Sentiment Becomes a Threat?
One of the key methods used by our software and our analysis team to tell whether or not a comment is a threat that needs more attention is the repetition of negative sentiment online by an individual or group.
For example:
Does a particular author of a comment or post have a long history of bad-mouthing an organisation or expressing negative sentiment?
Have they repeated the same negativity on multiple sources?
Even if they aren’t directly threatening any physical or tangible action against the organisation, if there’s enough online commentary from a single individual or group then this could escalate and it may be smart to further monitor.
You can then set up a search using our filters to target this individual or group so that you don’t miss if this negative sentiment becomes a physical or reputational threat.
Secondly, using Spotlight, users can identify posts expressing dangerous emotions such as anger, or disappointment. Both if repeated enough should be addressed. Posts expressing anger are likely to indicate a physical threat and should be monitored for that, whilst the posts expressing disappointment may hold reputational risks.
Summary
Sentiment analysis tools like Signal’s Spotlight can help security teams form a broader and more detailed overview of the situation to better understand the potential and emerging threats. It allows them to target their online searches and cut through the noise to identify key threats. All of this essentially means a more efficient and more effective security team.
You also might like:
Critical Security Intelligence for the Financial Services Sector
Critical Security Intelligence for the Financial Services Sector
Whether it’s detecting and managing physical threats to assets, or aiding cybersecurity teams with efficient methods for open and dark web monitoring, Signal threat intelligence software plays a crucial part for a number of businesses operating in the financial services sector.
A Financial Services Use Case
Since its conception Signal is proud to have developed a strong use case across the financial sector. Proving to be an invaluable tool for a number of financial services organisations including several multinational and Fortune 1000 companies.
Signal open source threat intelligence platform now forms an integral part of their security teams’ toolbox, assisting across concerns, from detecting and managing physical threats to assets, reputation or VIPs, to aiding cybersecurity teams with efficient methods for open and dark web monitoring.
Physical Security
Using Signal, insurance providers, financial companies, and banking organisations can not only gain an overview of emerging threats in real-time but also target key areas and assets that they want to closely monitor creating a hyper-relevant stream of actionable real-time data.
For example, banking organisations use Signal to monitor geo-located information online, focusing their web monitoring on key locations of particular interest such as ATMs, head offices, or VIP locations. They can additionally run the focused data that surfaces through our sentiment analysis software. This allows them to help cut through the noise and quickly identify online chatter expressing negative sentiment so that they can more efficiently distinguish threats.
A secondary use of Signal for the financial services sector is monitoring their competitors’ security threats which may also be affecting them - even if they don’t know it yet. This allows their security teams to predict potential threats even before they emerge.
How Signal has been used in the Banking Sector to Detect and Deter Threats
In 2019, one of Signals clients was able to prevent a particularly worrying case of attempted fraud. An employee at that bank was being harassed online in an attempt to instigate said employee to provide confidential information of customers to hackers for use in fraudulent activity.
Thankfully, Signal was able to spot this before matters progressed, preventing potentially hundreds of thousands of dollars worth of damages.
Signal has also been used to pinpoint worrying sentiment against some of our customer’s executive teams.
Cyber Security Threats
Signal is also used by customers for cybersecurity intelligence to determine risks such as:
Fraudulent statement packs;
Fake bank statements;
Phishing websites (using our in-built image recognition);
Credit card and account credentials for sale on the dark web.
Security teams use Signal to monitor both open and dark web conversations. This enables them to keep abreast of new and developing global trends and methods used in cyber fraud which is effecting their industry as a whole. Using this data they can actively develop strategies to prevent and tackle new and rising methods of cybercrime.
Signal also allows these teams to monitor for data breaches by alerting security teams as soon as chat is identified around potential data breaches which could affect the organisation itself, or their customers.
Ways Signal Helps Financial Services
Identify negative sentiment and potential threats to customer assets.
Detect and intercept stolen credit card and account credentials for sale on the dark web.
Monitor targeted locations to create a focused stream of actionable real time data.
Signal allows our customers to analyse emerging global trends, detect threats in real-time and then form appropriate security strategies to counter these potential threats as or even before they fully reveal themselves.
For the financial services having this targeted and focused stream of accurate and relevant data is vital to ensuring the safety and security of their customers, assets, and employees.
People are selling your stolen data online. Here's what it looks like
It was only on March 13th, two months after their systems were breached and sensitive data was stolen, that Kathmandu publicly responded to the breach; intelligence software like Signal could have instantly spotted people trying to sell the stolen data online and led to a much faster response time.
The image below shows a typical message from a carrier of stolen financial information looking for a buyer.
Using Signal open source intelligence software, we found this on the dark web.
Hackers will go wherever the money is, from NZ to Europe to the US or – as in this case – Australia.
They also recently attacked New Zealand, where equipment and clothing retailer Kathmandu suffered a data breach at the start of 2019. Intruders took customers’ credit card and personal information.
The ASX-listed Kathmandu said the following in a public statement on March 13:
“Kathmandu has recently become aware that between 8 January 2019 and 12 February 2019, an unidentified third party gained unauthorised access to the Kathmandu website platform. During this period, the third party may have captured customer personal information and payment details entered at check-out.”
It was only March 13th that Kathmandu publicly responded to the breach; intelligence software like Signal could have helped spot people trying to sell the stolen data online.
Doug Hunt of Auckland described on social media how on February 15 $2581.72 was taken from his credit card account. A second fraudulent transaction was noticed by the bank and blocked.
Hunt says he found out about the breach only after his bank, ANZ, phoned him.
Hunt told media he was appalled it took Kathmandu a month to respond.
Who hackers are and how they operate
Taking credit card numbers is one of many ways hackers make money. Another is to get ATMs to spew cash.
Jackpotting attacks can empty ATMs in minutes and are performed by prying open a panel to access a USB port on the machine and injecting malicious code, Tech Republic reports. Jackpotting has been a growing security threat in Europe and Mexico.
Most ATMs can be hacked in under 20 minutes, according to Zero Day. Typically splicing a black box into the cable between the ATM’s computer and cash dispenser is the way it’s done.
Another way is by plugging a flashdrive into one of the ATM's USB or PS/2 ports then running commands on the operating system to cash out money.
There’s also malware. North Korean-linked Lazarus Group (aka Hidden Cobra) is believed responsible for malware known as FASTCash which stole $13.5 million from India’s Cosmos Bank between August 10 and August 13, 2018. That group committed thousands of fraudulent ATM transactions across 28 countries and came down to three unauthorized money transfers using the SWIFT international financial network.
Data breaches can be stopped before they happen
The Ponemon Institute’s 2018 IBM Cost of a Data Breach study reported the average time it takes to identify a data breach is a shocking 196 days.
The time it takes Signal security intelligence to identify a potential breach being arranged on the dark web: minutes. Australian and New Zealand banks, institutions, businesses, hospitals and ASX/NZX-listed companies can all receive early indicators so you can be proactive about security and not caught off guard.
If you know potential threats, you can set your own search terms
Signal is an extremely user-friendly app and can be utilised by any staff members with minimal training. Simply put in the search terms you feel your institution needs to monitor; Signal’s easy interface then provides alerts when what you’re looking out for appears online.
Signal is designed to recognise conversations in which criminals name your bank or business
Every day, Signal observes and captures data around Dark Web users offering to sell stolen material
Signal parses through postings and conversations and can spot questionable behaviour which might harm your brand, your interests or even your staff.
Breaches happen to many different types of online businesses
LinkedIn lost 6.5 million encrypted passwords in 2012;
Ashley Madison had 36 million accounts compromised in 2015. In July that year, a group calling itself ‘The Impact Team’ threatened to release users' names and personally identifying information if Ashley Madison would not immediately shut down. The group then leaked 25gb of company data, including user details causing huge embarrassment for the thousands of Saudi executives and US military and government employees who had accounts on Ashley Madison. The company which owns Ashley Madison then faced lawsuits, as users who had in the past asked Ashley Madison to delete their accounts found themselves caught up in the leak and sued the company.
Dropbox login data for 68 million users has been offered for sale on the dark web. The data set came from a 2012 breach. The trafficker was known in 2016 as TheRealDeal and offered a disturbingly low price: two bitcoins.
Which data is valued most?
Various online computer hacking magazines estimate the value of stolen information like so:
Passports are estimated to be worth $2,000
Medical records: $1,000
Online payment account credentials typically valued at up to $200
Credit or debit card information – usually sold for up to $110
Diplomas: $400
Trend Micro research shows the main types of data stolen are financial and insurance data, which can be twisted to then become a tool for blackmail; healthcare details; payment card information; account logins; and educational information such as transcripts.
However, even supposedly valueless data such as a username and password login to a seemingly unimportant website offers value to cybercriminals through the credential stuffing tactic. This is when cybercriminals use user logins against multiple different login forms due to the fact that many people use the same password for multiple websites.
We have dozens of examples of top share listed companies relying on Signal software to avert risk.